Hey there! Welcome to the blog!
Contents
- Insight on AWS Detective
- What is Amazon GuardDuty?
- Amazon GuardDuty
- Key Features of GuardDuty
- Usage
- Costing for Amazon GuardDuty
- Amazon Detection Scenario Walk Through
Insight on AWS Detective
AWS features a specialized security feature called as AWS Detective. It is a security feature that exists to analyse, investigate, and aid in identifying the root cause of any suspicious activity. Once connected, the service automatically collects log data from your AWS resources and uses machine learning (ML), statistical analysis, and graph theory to build a linked dataset that you can use to conduct more efficient security investigations.
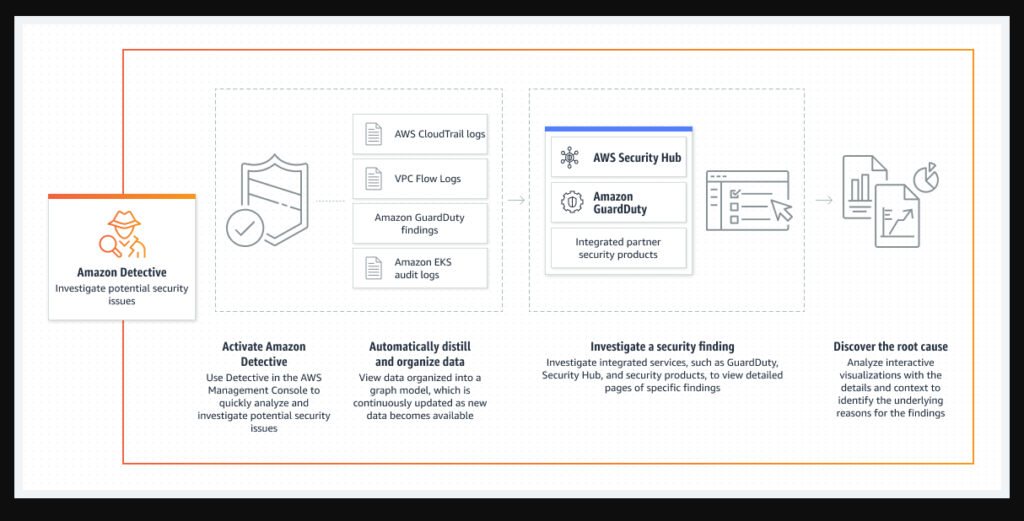
AWS Detective collects, and analyses trillions of events and data sources such as VPC Flow Logs, AWS CloudTrail, Amazon GuardDuty, EC2 and various logs to create an interactive view of all your resources, users and interaction between them over a detailed timeline. It provides visual data representation of all your resources and highlights the details of the resources that may require correction.
In order for Amazon Detective to be enabled, it requires Amazon GuardDuty to be enabled 48 hours prior, as this allows GuardDuty to collect and analyse the processing data.
What is Amazon GuardDuty?
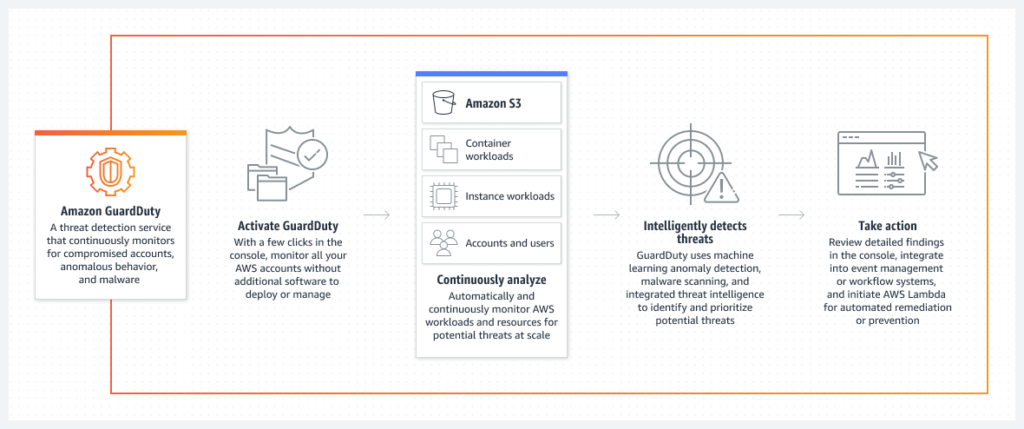
Amazon GuardDuty is an intelligent threat detection service that continuously monitors your AWS accounts and workloads for malicious activity and delivers detailed security findings for visibility and remediation. Expose threats quickly using anomaly detection, machine learning, behavioral modelling, and threat intelligence feeds from AWS and leading 3rd-parties.
They utilize data such as
- Network traffic – GuardDuty alerts the user about high incoming and outgoing traffic records
- AWS Account Activities
- Irregular IP Matching
Let’s try to initialize Amazon GuardDuty
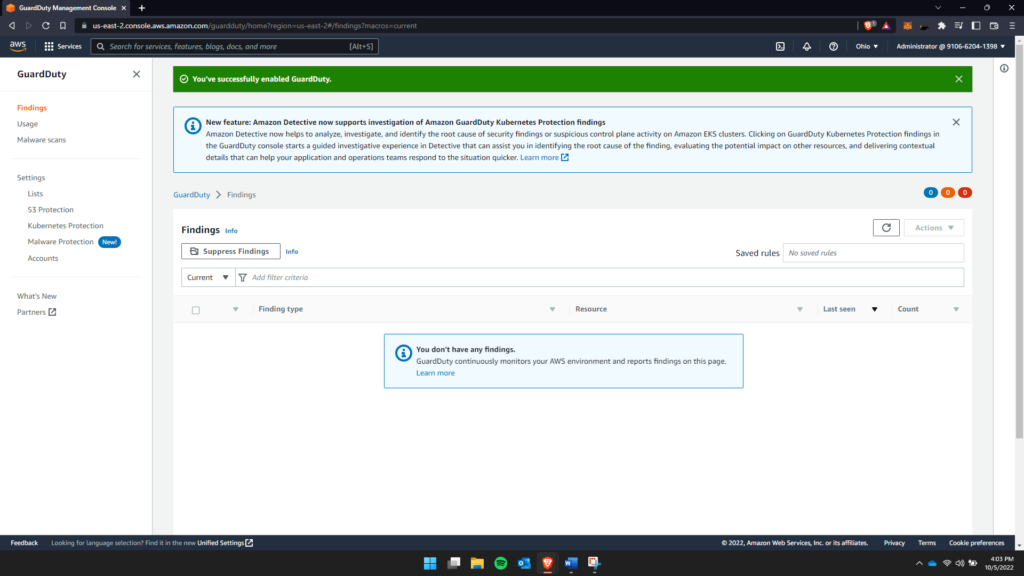
To enable your GuardDuty, all you have to do is the following:
Console Home > Services > Security, Identity & Compliance > GuardDuty > Click Enable
To your right, you see that my GuardDuty has been enabled.
Adding accounts into GuardDuty
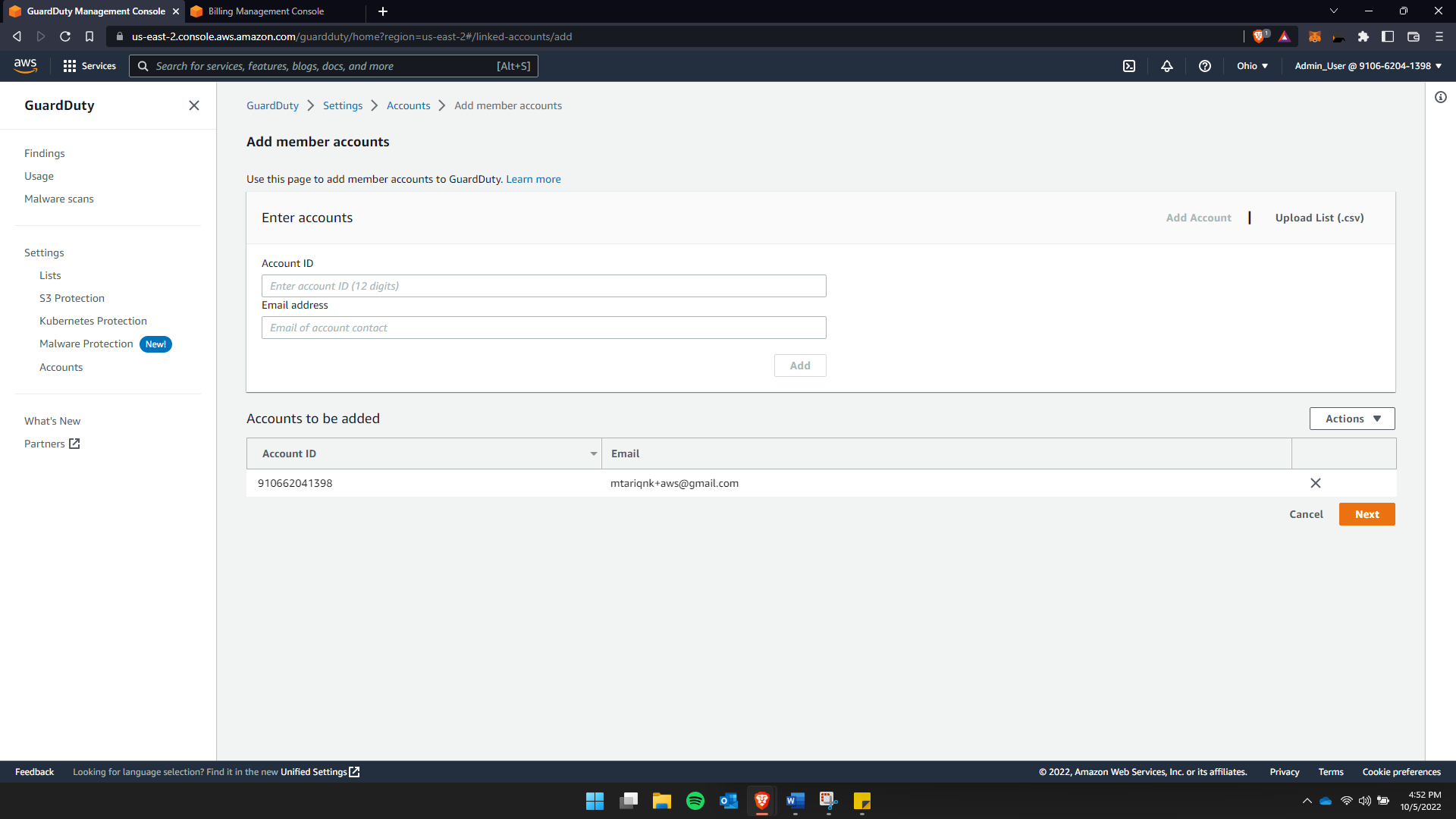
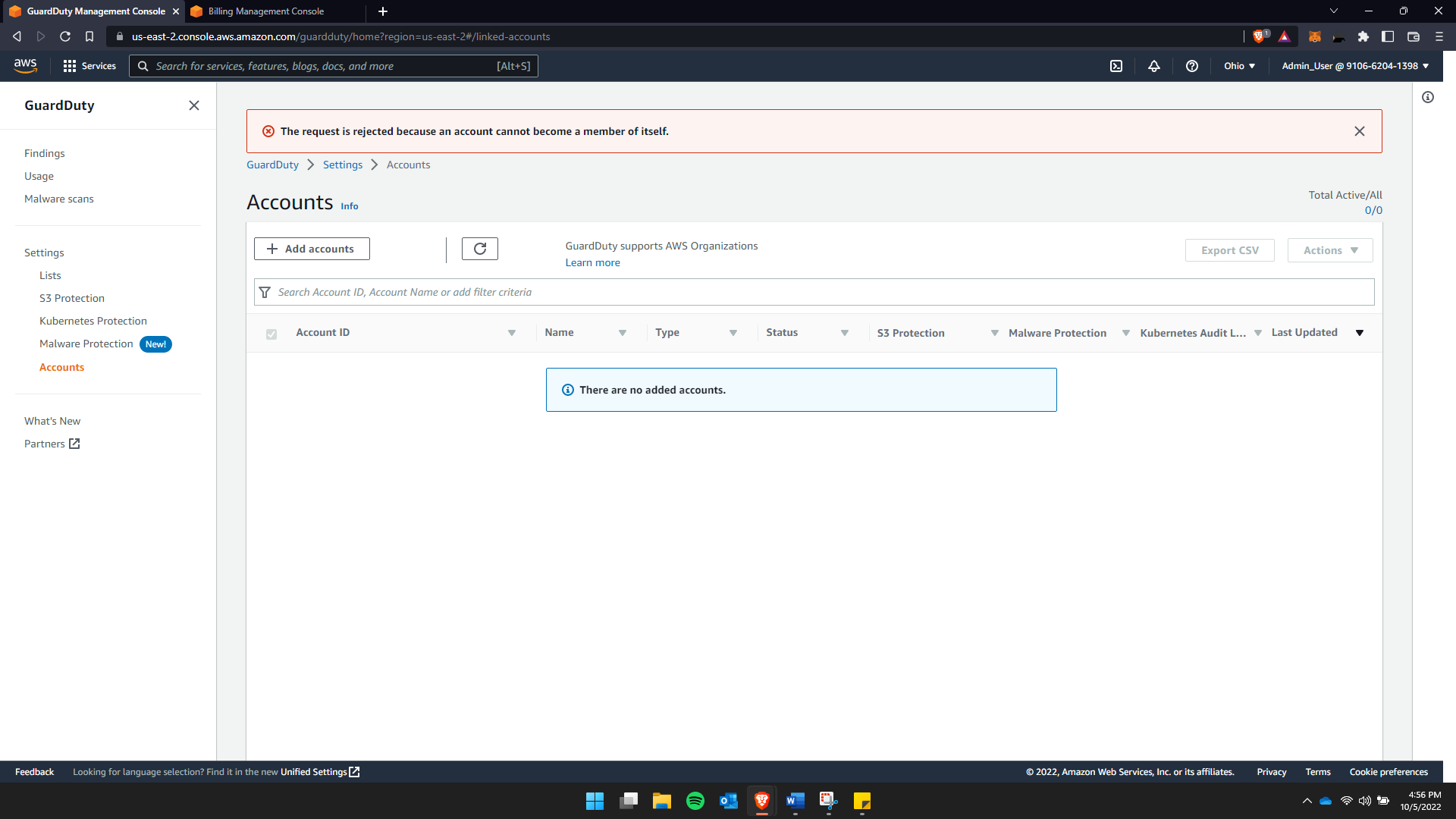
In the images attached above, you see that the user is trying to add accounts to the secure list. During this stage that the administrator can specify the security terms and condition as per requirements for each IAM. GuardDuty
It generated an error in my case because that was my account ID, as GuardDuty is enabled.
Key Features of GuardDuty:
1. List Management –
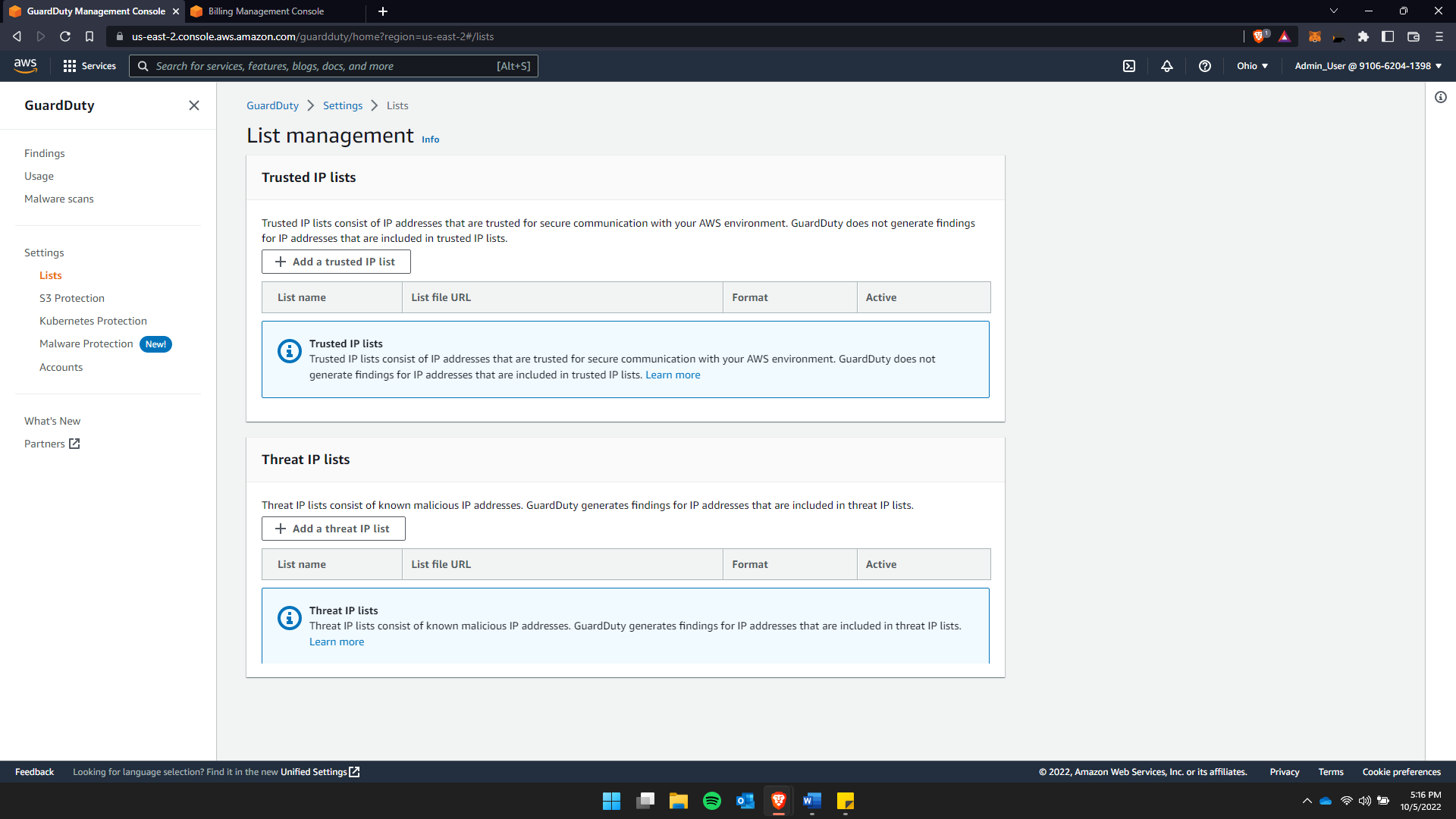
GuardDuty possess a setting that allows user to differentiate between trusted or threat IP addresses. This provides a safe AWS environment and secure connection between the user and the GuardDuty firewall.
…> GuardDuty > Settings > List Management
2. S3 Protection –
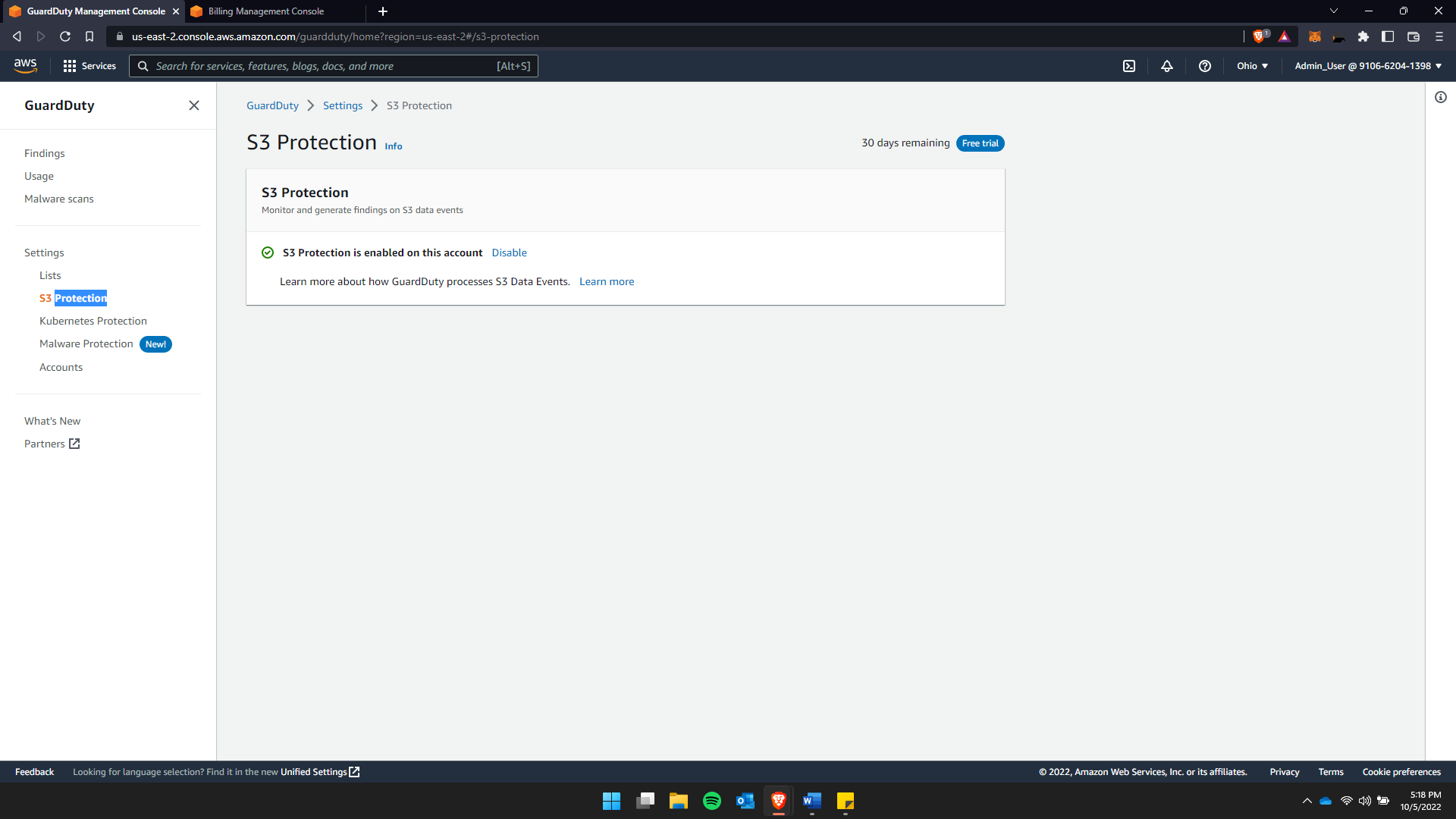
S3 is an object storage service by AWS. This service allows users to store data, log files, application files, images, and videos. To secure this GuardDuty monitor the timeline and generates findings on all ongoing S3 events.
…> GuardDuty > Settings > S3 protection
3. Kubernetes Protection
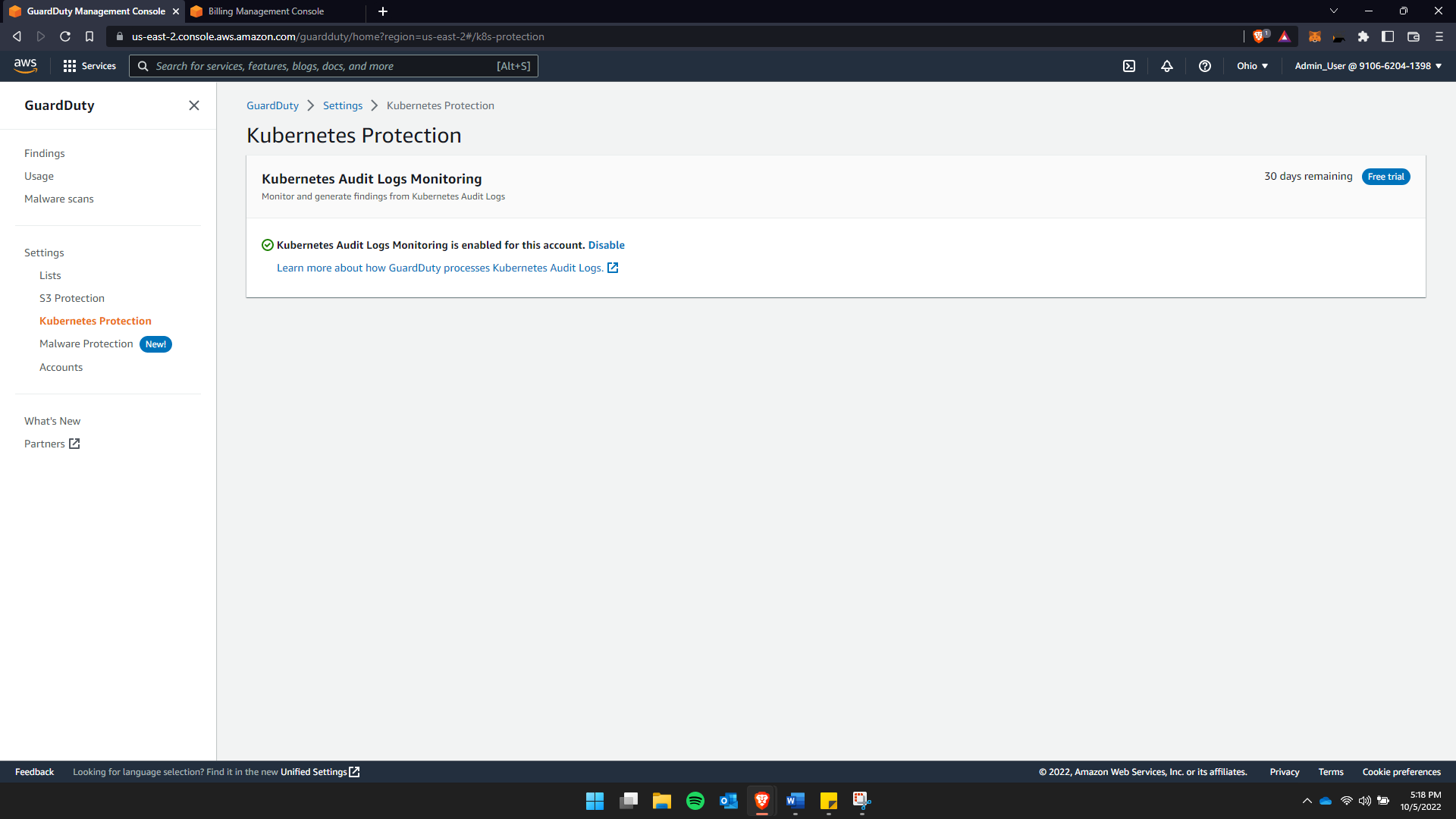
GuardDuty generates Monitor and generate findings from Kubernetes Audit Logs allows users to define the difference between trusted IP list and threat IP list.
…> GuardDuty > Settings > Kubernetes Protection
Usage
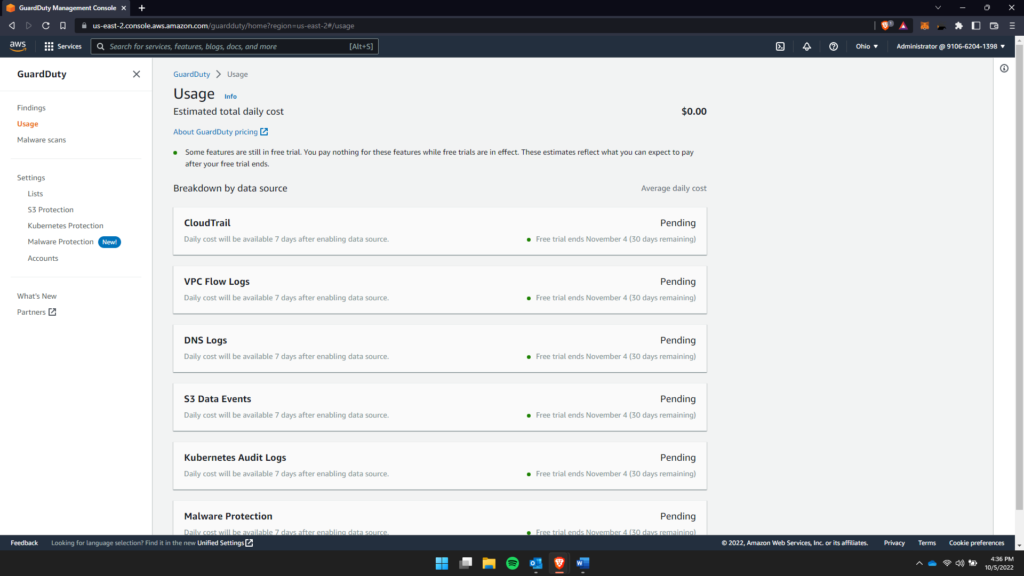
The data retrieved by the GuardDuty is collected and organized into the categories of other services. This services are further broken down into the detail logs, events and processes taking place.
In the above image, the reason you see $0.00 in addition to other options showing pending status is because of the AWS Free tier – that provides these services for a period 30 days.
Costing for Amazon GuardDuty
| Services | Cost |
|---|---|
| AWS CloudTrail Management Event Analysis | |
| Per one million events / month | $4.00 per one million events |
| AWS CloudTrail S3 Data Event Analysis | |
| First 500 million events / month | $0.80 per one million events |
| Next 4,500 million events / month | $0.40 per one million events |
| Over 5,000 million events / month | $0.20 per one million events |
| Amazon EKS Audit Logs | |
| First 100 million events / month | $1.60 per one million events |
| Next 100 million events / month | $0.80 per one million events |
| Over 200 million events / month | $0.20 per one million events |
| VPC Flow Log and DNS Query Log Analysis | |
| First 500 GB / month | $1.00 per GB |
| Next 2,000 GB / month | $0.50 per GB |
| Next 7,500 GB / month | $0.25 per GB |
| Over 10,000 GB / month | $0.15 per GB |
| EBS Data Volume Scan Analysis | |
| Per GB / month | $0.03 per GB |
Amazon Detection Scenario Walk Through
Below attached is an in-depth walk through of working AWS Detective: