- Security alerts and incidents
Azure alerts the notifications that are generated by defender for cloud and defender for cloud plans when threats in your cloud.
- Security alerts are triggered by advanced detections in Defender for Cloud, and are available when you enable enhances security features.
- Each alert provides details of affected resources, issues, and remediation recommendations.
- Defender for Cloud classifies alerts and prioritizes them by severity in the Defender for Cloud portal.
- Alerts data is retained for 90 days.
- Alerts can be exported to CSV format, or directly injected into Microsoft Sentinel.
- Defender for Cloud leverages the MITRE Attack Matrix to associate alerts with their perceived intent, helping formalize security domain knowledge.
2. How alerts are classified?
Defender for Cloud assigns a severity to alerts to help you prioritize how you attend to each alert. Severity is based on how confident.
| Severity | Recommended response |
| High | There is a high probability that your resource is compromised. You should look into it right away. Defender for Cloud has high confidence in both the malicious intent and in the findings used to issue the alert. For example, an alert that detects the execution of a known malicious tool such as Mimikatz, a common tool used for credential theft. |
| Medium | This is probably a suspicious activity might indicate that a resource is compromised. Defender for Cloud’s confidence in the analytic or finding is medium and the confidence of the malicious intent is medium to high. These would usually be machine learning or anomaly-based detections, for example a sign-in attempt from an unusual location. |
| Low | This might be a benign positive or a blocked attack. Defender for Cloud isn’t confident enough that the intent is malicious and the activity might be innocent. For example, log clear is an action that might happen when an attacker tries to hide their tracks, but in many cases is a routine operation performed by admins. Defender for Cloud doesn’t usually tell you when attacks were blocked, unless it’s an interesting case that we suggest you look into. |
| Informational | An incident is typically made up of a number of alerts, some of which might appear on their own to be only informational. |
3. What is security incidents?
- A security incident is a collection of related alerts.
- Incidents provide you with a single view of an attack and its related alerts, so that you can quickly understand actions an attacker took, and resources affected.
- It’s challenging for security analysts to triage different alerts and identify an actual attack. By correlating alerts and low fidelity signals into security incidents, Defender for Cloud helps analysts cope with this alert fatigue.
- In the cloud, attacks can occur across different tenants, Defender for Cloud can combine AI algorithms to analyze attack sequences that are reported on each Azure subscription. This technique identifies the attack sequences as prevalent alert patterns, instead of just being incidentally associated with each other.
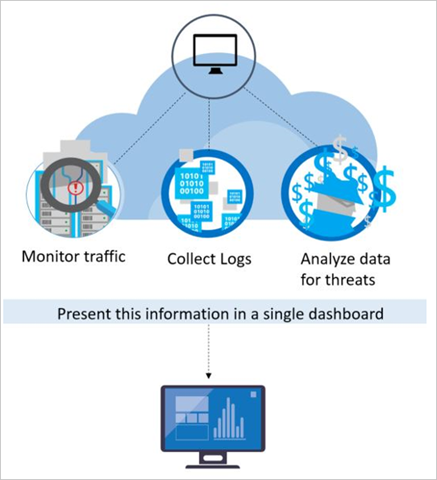
How does defender for cloud detect threats?
To detect real threats and reduce false positives, Defender for Cloud monitors resources, collects, and analyzes data for threats, often correlating data from multiple sources.