Introduction:
Hello! In this blog, I will be explaining a detailed article on Azure Bastion and How to create azure bastion.
I’m sure you’re familiar with RDP and SSH if you manage a remote server or virtual machine. RDP and SSH are both used to gain remote access to virtual machines and servers. RDP and SSH are also used to connect to virtual machines in cloud services such as Azure and AWS.
When you log in to your Azure account and go to Settings, you’ll see three options for connecting to your virtual machine: RDP, SSH, and BASTION. The screenshot below shows the three options.
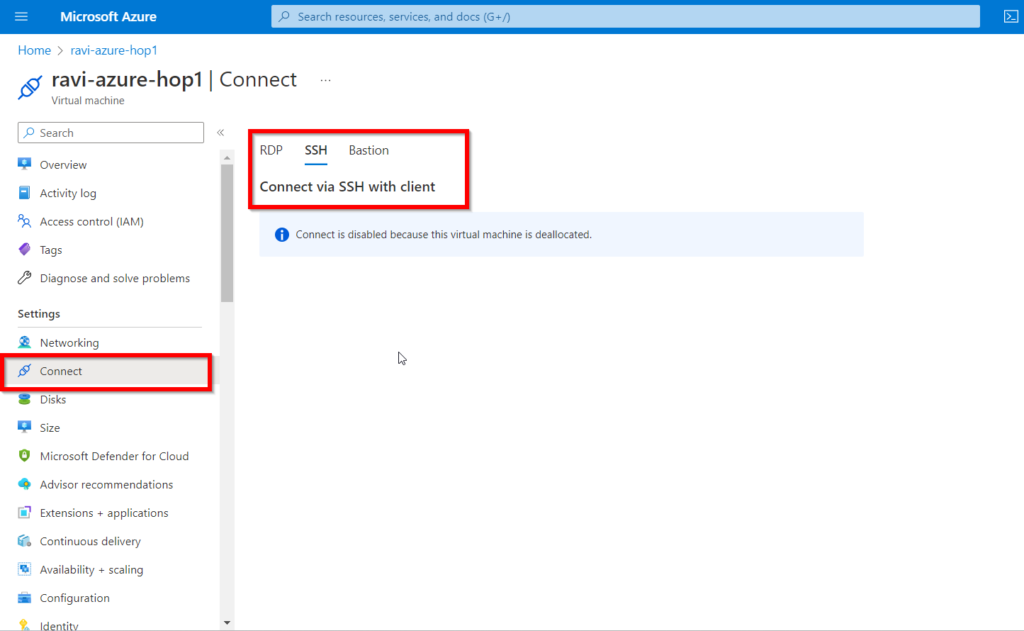
In this blog Let’s look at what Azure Bastion is and when and why you should use it to connect to your Azure virtual machine.
What is Azure Bastion?
Azure Bastion is a PaaS service that allows you to connect to Azure VMs via RDP/SSH without exposing them to the public internet. Azure Bastion is installed in a virtual network and supports virtual network peering. Azure Bastion, in particular, manages RDP/SSH connectivity to VMs created in the local or peering vNet.
Why Azure Bastion?
Previously, in order to connect to an Azure VM via RDP or SSH, you had to:
- Connect directly to the machine by exposing direct host ports.
- Use an intermediary, such as an RDP gateway, to “tunnel” through while still leaving ports open to the outside world.
- Connect to a “hop server” or “jump host” and then connect to the host again.
- To connect the Bastion host to an existing virtual network.
These options were not ideal because they required you to either create a security risk or go through a complicated connection process. Bastion changed everything. You can now set up a Bastion host that only exposes an HTTPS port to the outside world but can transparently tunnel RDP or SSH traffic to an Azure VM using the managed Azure Bastion service. Azure Bastion is a restricted and secure Azure VM designed solely for remote connectivity.
Traffic workflow when we connect Azure VMs.
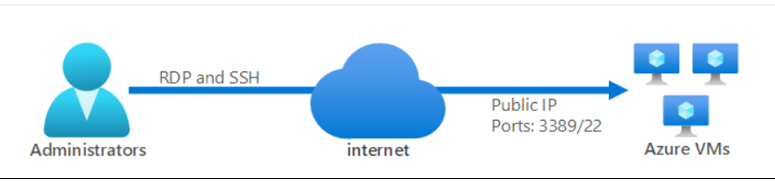
#Scenario 1 – The traffic flow when we use the public Internet to access VMs is shown below.
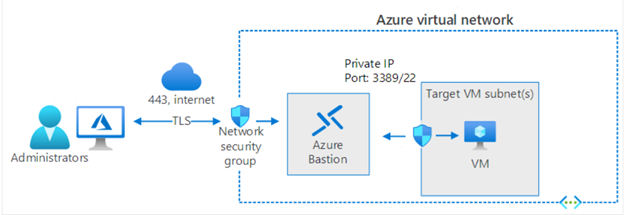
#Scenario 2 – The traffic flow when we use Azure Bastion to access VMs is shown below.
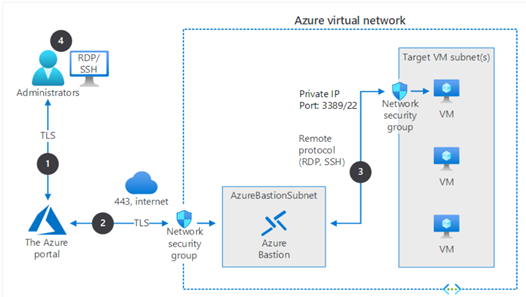
How does Azure Bastion work?
Azure Bastion is installed in the same virtual network as all Azure VMs. Even so, it has its own NSG-protected subnet called “AzureBastionSubnet,” with a minimum /27 prefix. The Bastion subnet only allows communication via TCP post 443 from Azure Portal.
RDP vs SSH vs Bastion
RDP (Remote Desktop Protocol) is a Windows protocol that allows you to connect to remote Windows virtual machines and servers. RDP necessitates the opening of a port on the remote machine, virtual machine, or physical server. RDP ports are frequently attacked by hackers and bots because they are frequently exposed to the Internet and publicly accessible. Companies frequently use a virtual private network (VPN) and some form of multi-factor authentication to protect RDP instances (MFA).
Note:
It is strongly advised not to use RDP without a VPN connection for security reasons. Also, ensure that no RDP sessions are active when you are finished by manually logging off RDP sessions.
SSH (Secure Shell) protocol, similar to RDP, allows a client machine to communicate with and transfer data to another machine (server). SSH has the advantage of protecting communication security and integrity through strong encryption.
SSH protocol is used in corporate networks for,
- Providing secure access for users and automated processes
- Interactive and automated file transfers
- Issuing remote commands
- Managing network infrastructure and other mission-critical system components.
The following diagram shows SSH communication between a client and a server (two computers).
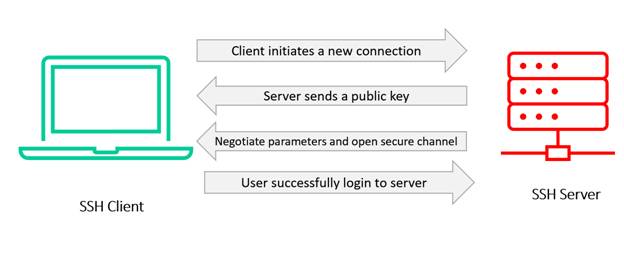
Azure Bastion is a new fully managed PaaS service that you can deploy within your virtual network. It enables secure and seamless RDP/SSH access to your VMs directly from the Azure portal via SSL. Your virtual machines do not require a public IP address when connected via Azure Bastion.
Key features of Azure Bastion:
— RDP and SSH directly in the Azure portal: Using a single click, you can access RDP and SSH sessions directly in the Azure portal.
— Remote Session over TLS and firewall traversal for RDP/SSH: Azure Bastion employs an HTML5-based web client that is automatically streamed to your local device, allowing you to connect to your RDP/SSH session via TLS on port 443, allowing you to securely navigate corporate firewalls.
— No need for a public IP address on the Azure VM: Azure Bastion connects to your Azure virtual machine via RDP/SSH using your VM’s private IP address. A public IP address is not required for your virtual machine.
— No need to worry about NSG management: Azure Bastion is an Azure fully managed platform PaaS service that has been internally hardened to provide secure RDP/SSH connectivity.
— On the Azure Bastion subnet, no NSGs are required. Because Azure Bastion connects to your virtual machines using a private IP address, you can configure your NSGs to only allow RDP/SSH from Azure Bastion. This eliminates the need to manage NSGs every time you need to securely connect to your virtual machines.
— Protection against port scanning: Because your virtual machines are not exposed to the public Internet, they are safe from port scanning by rogue and malicious users located outside your virtual network.
— Protect yourself from zero-day exploits. Hardening in a single location: Azure Bastion is a PaaS service that is fully managed by the Azure platform. Because it is located at the virtual network’s perimeter, you do not need to worry about hardening each virtual machine in your virtual network. By keeping the Azure Bastion hardened and always up to date for you, the Azure platform protects against zero-day exploits.
How to Set Up an Azure Bastion to Connect to a Virtual Machine?
I’ve provided a step-by-step procedure with screenshots below.
Requirements for Creating an Azure Bastion:
- Before we can create an Azure Bastion, we must first create an Azure account in the Azure portal. Here is a link to a step-by-step guide for creating an Azure account.
- we must Create an Azure virtual machine. Here is a link to a step-by-step guide for creating an Azure VM.
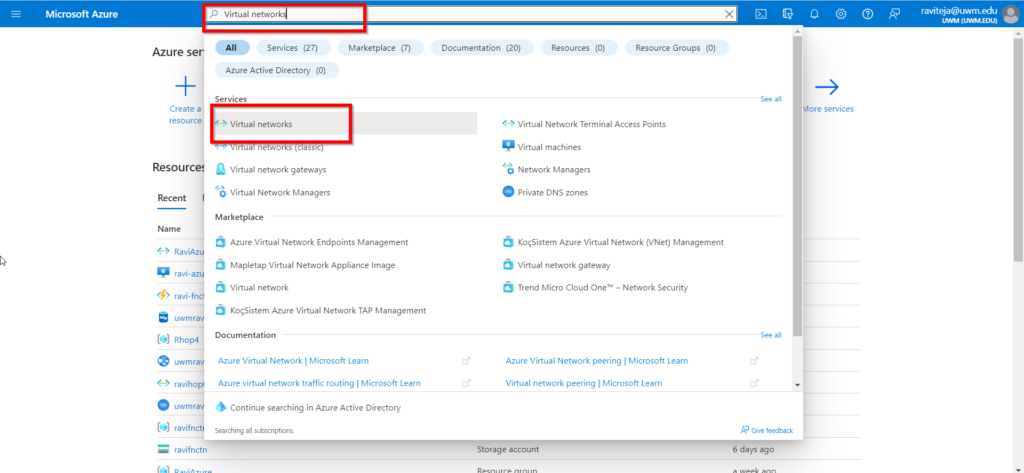
Step 1: Create a Virtual Network
The virtual network that will host the Bastion resource. During this process, you can either create a new virtual network in the portal or use an existing virtual network. If you’re using an existing virtual network, make sure it has enough free address space to support the Bastion subnet requirements.
- Go to Azure Portal and search for Virtual Networks.
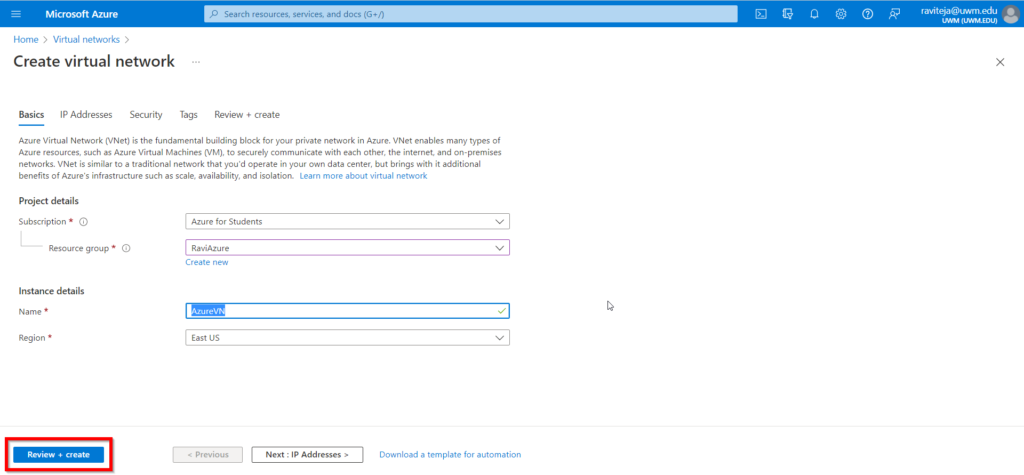
- Click on Create Virtual network button, enter the required details and click on the Review + Create button.
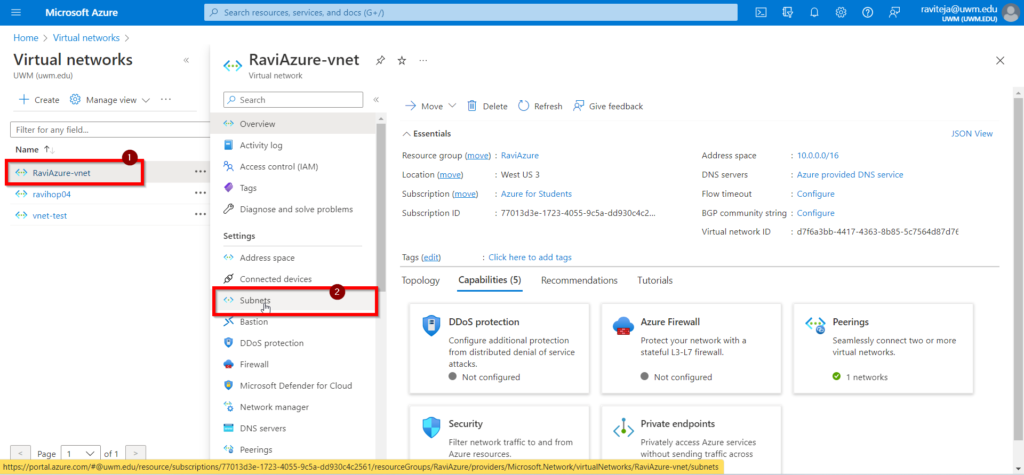
Step 2: Create a New Subnet for Bastion services:
- Select the Virtual network that you created in step 1.
- Choose Subnets from the list on the left.
- Create a new Subnet for Azure Bastion
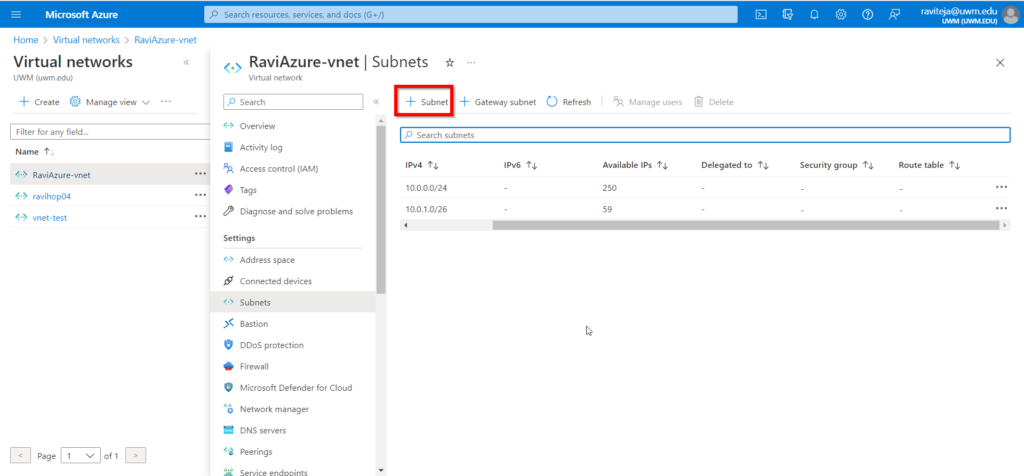
- Name the subnet as AzureBastionSubnet
- The subnet must be at least /26 (/26, /25, /24, and so on).
- Click on the Save button.
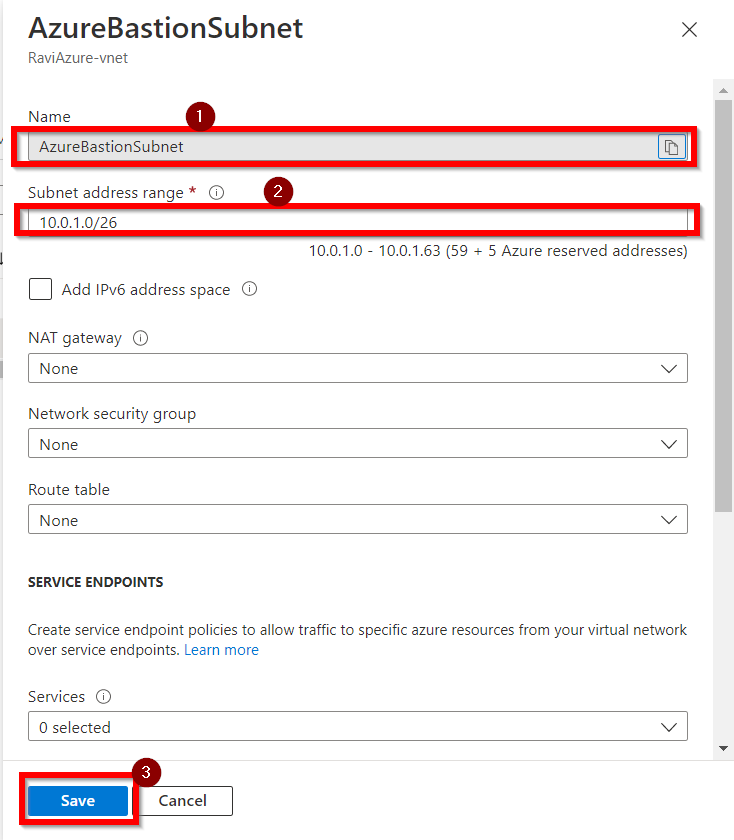
- On the Subnets page, you can now see the newly created AzureBastionSubnet.
Step 4: Create Bastion services:
- Search for Bastion on the Azure Portal’s home page.
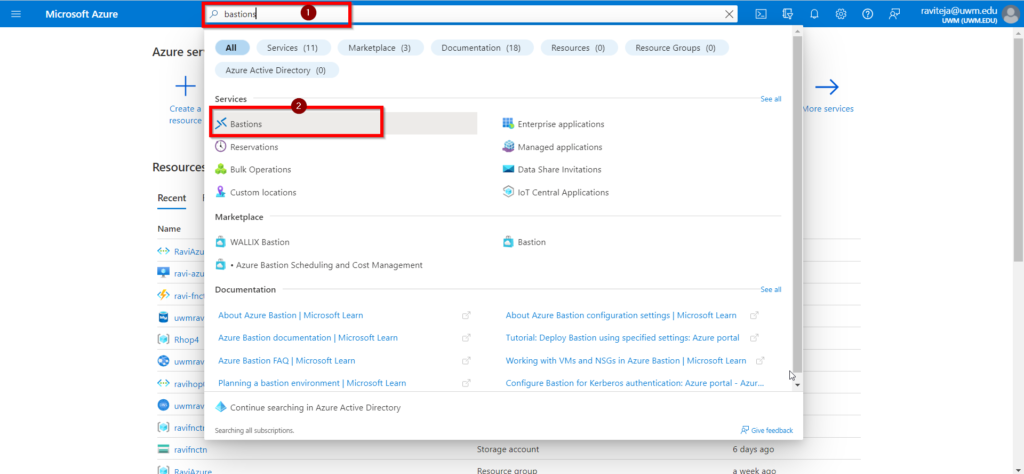
- Select Create button.
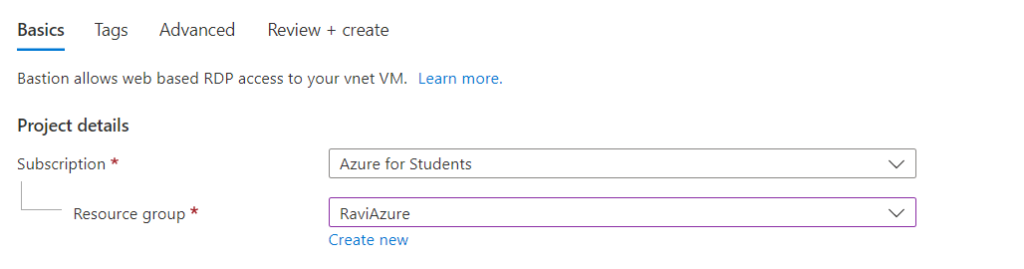
- Next, choose your subscription and a resource group in which to create the Azure Bastion host, or click Create new to start from scratch.
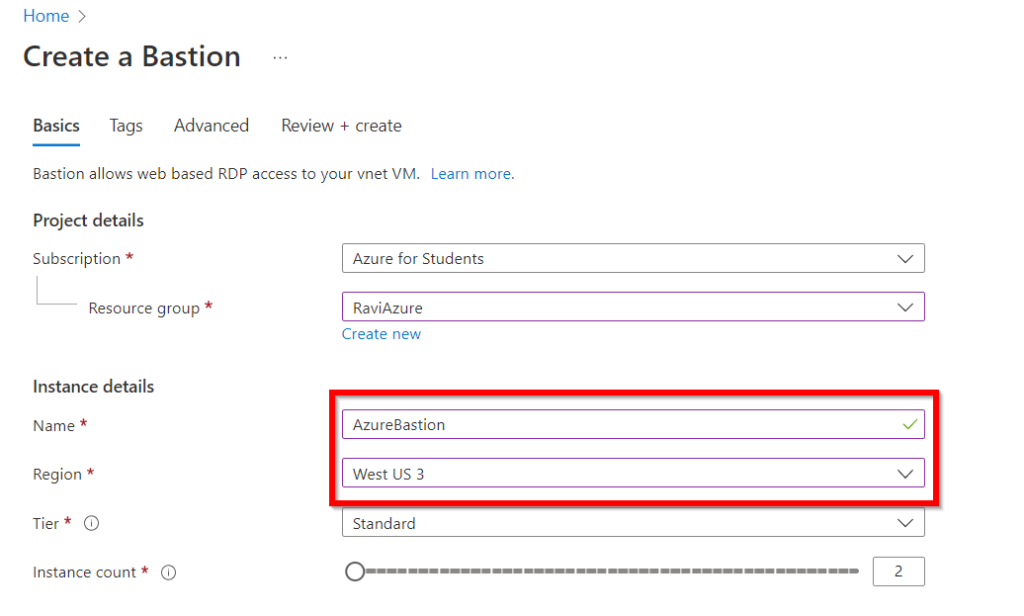
- A name for your preferred Bastion host.
- The region where the Bastion will be built, Choose the location where you created your Virtual network. (Refer to Step 1)
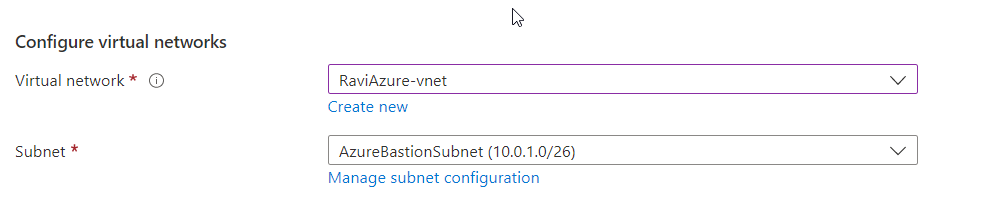
- Select Subnet from the Virtual network that you created in Steps 1 & 2.
- If you want Azure to generate a public IP address for you, give it a name. You can choose any name you want or use an existing one.
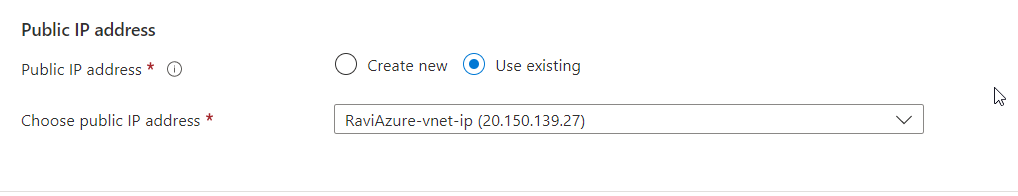
- After you’ve assigned all of the necessary Bastion attributes, click the Review + create button.
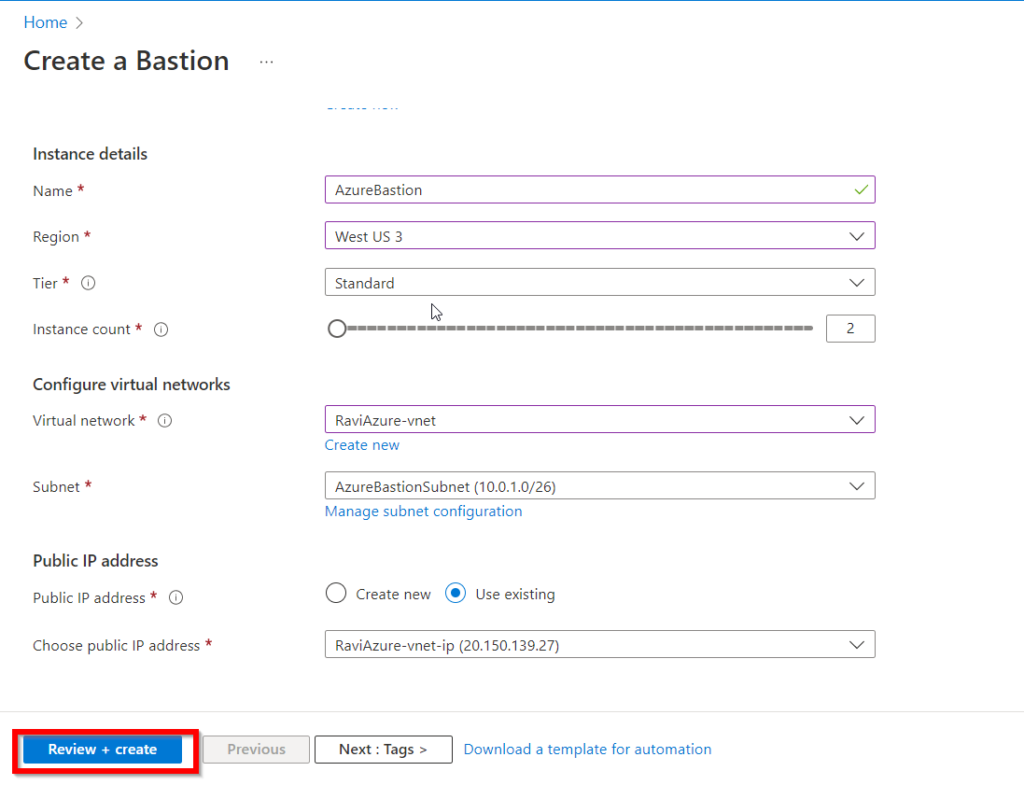
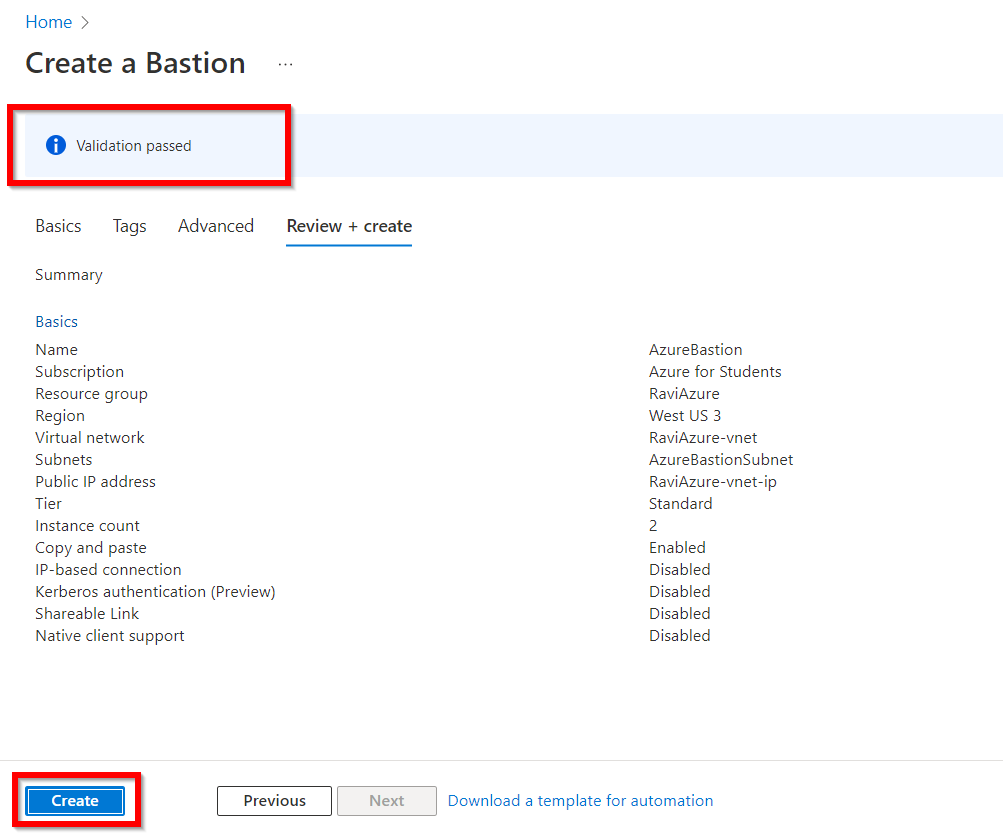
- Following the click of the Review + Create button, the system will validate
- When the validation pass, click the Create button to instruct Azure to start creating the Bastion resource.
- After clicking the Create button, the deployment will begin and will take some time to complete.
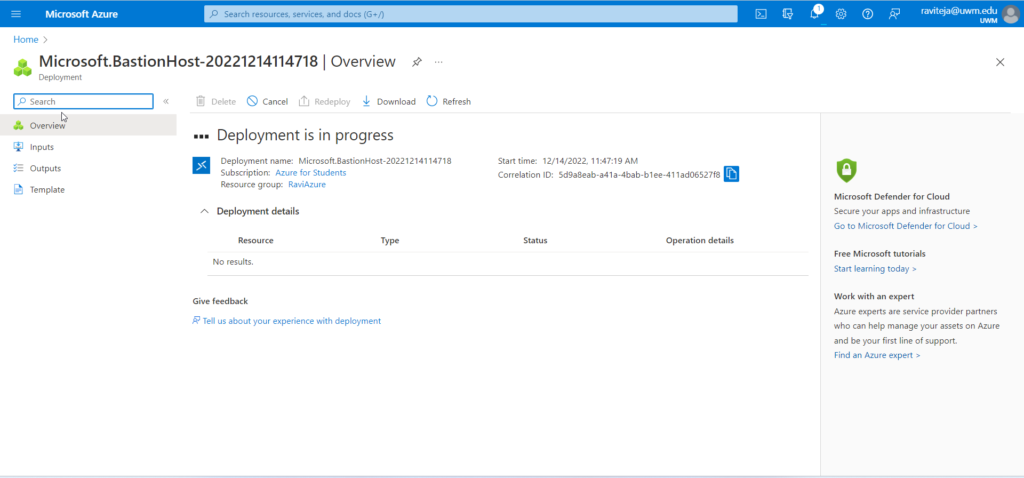
- It will complete the deployment after some time.
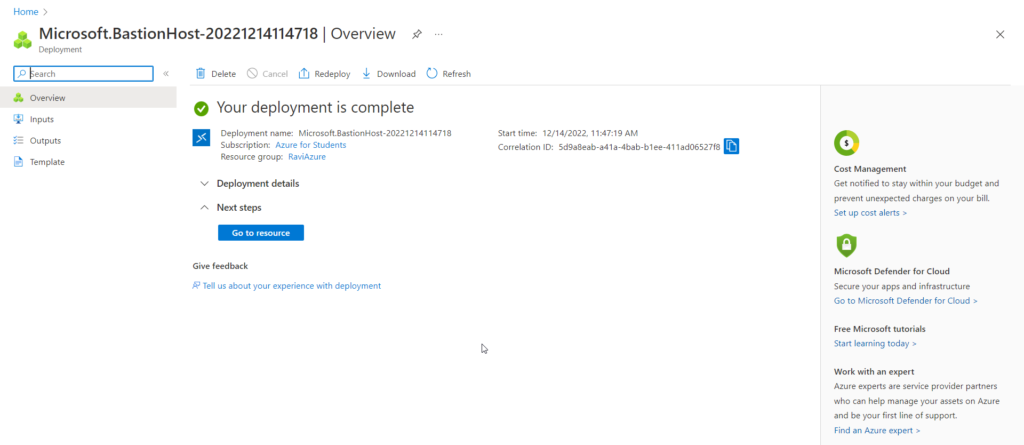
- Azure finished building the Bastion.
Using Azure Bastion to connect to an Azure VM:
After you’ve set up a Bastion resource, it’s time to see how you can use it to secure access to your Azure VMs. Assuming you’ve already set up an Azure VM per the prerequisites, let’s look at how to use Azure Bastion to connect to a Windows VM via RDP.
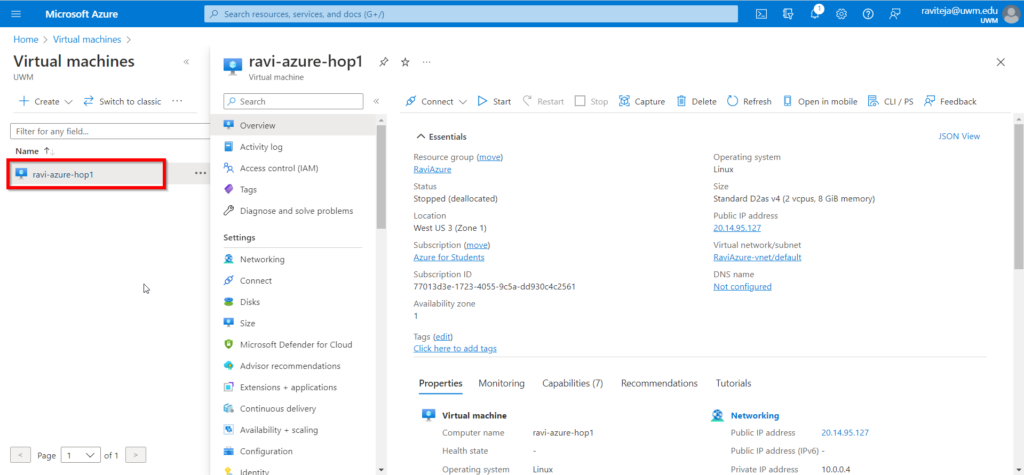
- Locate the Azure VM to which you want to connect using Azure Bastion.
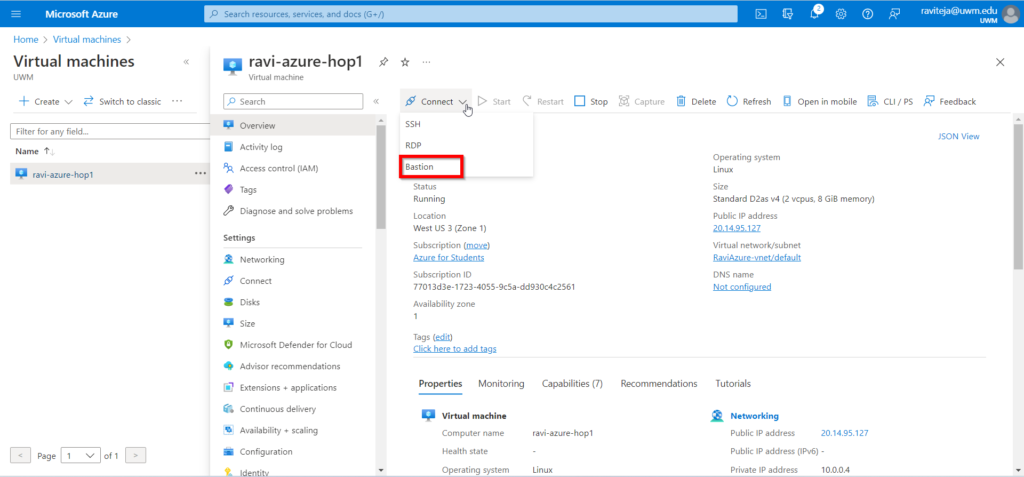
- Select Bastion from the Connect menu.
- To connect to the VM, on the Connect page, click the Use Bastion button and enter the username and Authentication type(if you used the Password while creating the VM Use the password here or the SSH Private key from the local file .)
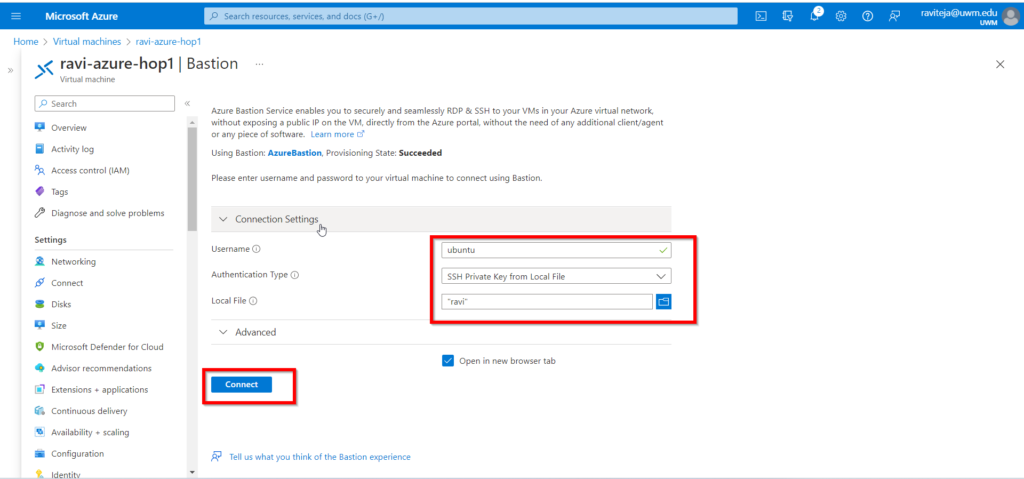
- Select Connect, and Azure will open a new browser tab displaying your VM’s desktop.
That’s all! You are now securely connected to your VM via RDP via your Azure Bastion host, all in your browser.
Conclusion:
So after going through the article you could see how much more convenient Azure Bastion is comparatively and how it is an excellent solution for securing RDP or SSH access.