Topics covered in this blog-
- What is Azure DDoS Attack?
- Why do these Attacks happen?
- Types of DDoS Attacks.
- DDoS Protection offerings(Basic & Standard).
- How does Azure DDoS Protection Standard Work?
- DDoS Protection Reference Architecture.
- Comparison between DDoS Protection Basic & DDoS Protection Standard Plans.
- Features of DDoS Protection.
- Testing DDoS Protection.
- Preventing a DDoS Attack.
- Pricing.
- Pros & Cons of DDoS Protection.
What is Azure DDoS Protection?
Distributed denial of service (DDoS) attack is considered to be one of the largest security concerns faced by customers in the cloud regions. A DDoS attack attempts to exhaust an application’s resources, making the application unavailable to legitimate users. That doesn’t mean to be in the range of terabits per second to take down an application but any specific targeted attack can impact the availability of an application running in Azure, which is receiving traffic from the public internet.
From early 2020 to 2021, we have seen a 341% growth in the number of DDoS attacks. This is mainly because the pandemic forced many businesses to go digital, which naturally made them more susceptible to cyberattacks.
Definition of DDoS – In a DDoS attack, a perpetrator intentionally floods the system, like a server, website, or other network resources, with illegitimate traffic. The computers are connected in a coordinated command-and-control network, called a botnet. A malicious third party controls the botnet to launch the DDoS attack. By overwhelming the service’s capabilities, the activity triggers a denial of services to legitimate users. DDoS attacks can be targeted at any endpoint that’s publicly reachable through the internet.
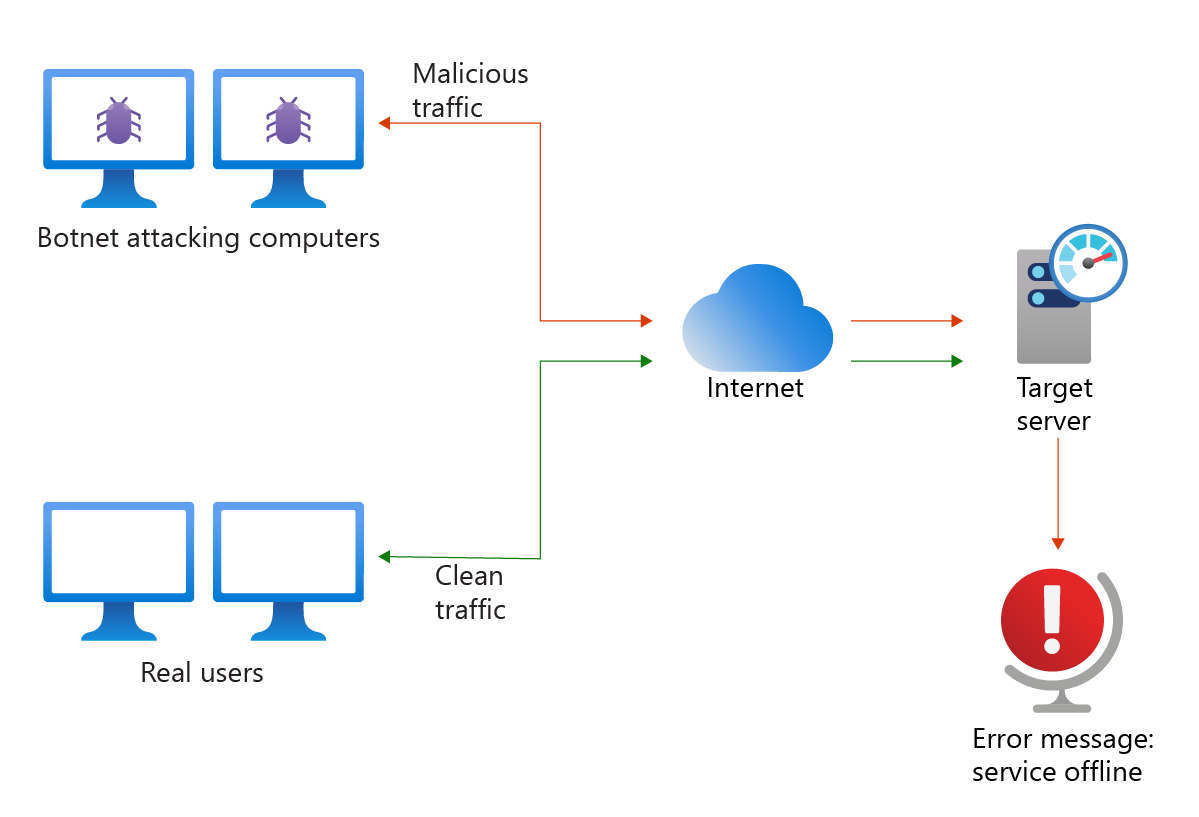
Why do these attacks happen?
Some of the main reasons for DDoS attacks are:
- Ransom: Attackers demand ransom after the DDoS attacks. In some cases, hackers would send the note to organizations beforehand in order to increase the ransom.
- Hacktivism: DDoS attacks are also used to raise the voice in cases of injustice.
- Competition: A 2017 survey revealed that over 40% of companies hit by a DDoS attack blame their competitors.
Types of DDoS Attacks:
- Volumetric attacks:
These attacks use multiple infected systems in order to flood the network layer(L3 of OSI) with a considerable amount of fake traffic. In most cases, the systems which are compromised would be multiple botnets.
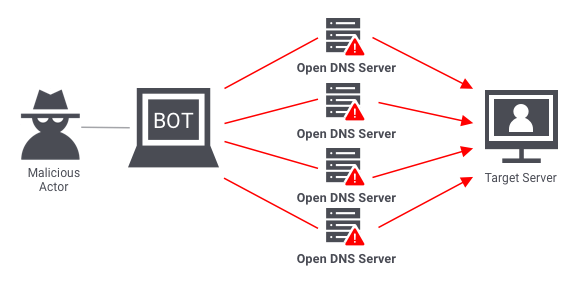
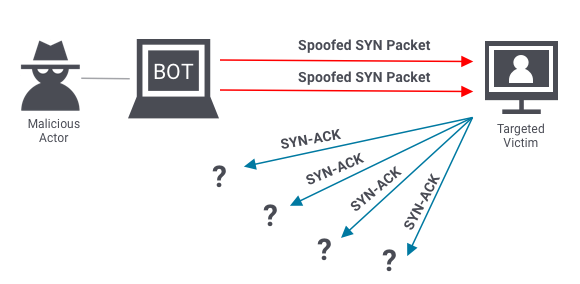
- Protocol attacks:
These attacks target Layer 3(Network) or Layer 4(Transport) of the OSI model. They exploit a weakness in TCP. The attacker sends a succession of TCP SYN requests, ignoring the SYN+ACK reply. This attack is directed towards a target to overwhelm the target and make it unresponsive.
- Application layer attacks:
The application layer attack is where the server generates the response to an incoming client request. For example, if a user enters http://www.amazon.com/products on their browser, an HTTP request is sent to the server, requesting the products page. Then the server will fetch all the information related to the page, package it in response, and send it back to the browser. These type of attacks occurs mostly when a hacker uses different systems to repeatedly request the same source from the server eventfully leading to maximizing the capacity of the server.

Azure DDoS Protection offerings(Basic & Standard)
DDoS Protection Basic
Azure provides continuous protection against DDoS attacks. DDoS protection does not store any customer data. At no additional cost, Azure DDoS Protection Basic protects every Azure service that uses public IPv4 and IPv6 addresses. This DDoS protection service helps to protect all Azure services, including platform as a service (PaaS) services. DDoS Protection Basic requires no user configuration or application changes.
DDoS Protection Basic provides:
- Active traffic monitoring and always-on detection. DDoS Protection Basic monitors your application traffic patterns all day, every day, searching for indicators of DDoS attacks.
- Automatic attack mitigation. Once the attack is detected, it’s mitigated.
- The DDoS Protection Basic service level agreement (SLA), which is based on the Azure region with best-effort support.
DDoS Protection Standard
DDoS Protection Standard provides enhanced DDoS mitigation features to defend against DDoS attacks. The following list describes the features of DDoS Protection Standard:
- It provides native integration into the Azure portal for setup and deployment.
- When DDoS Standard is enabled for a virtual network, all resources on that network are automatically protected.
- Network resources are always to be monitored and when malicious software is detected the alerts will be notified.
- It helps to secure layers 3(network) and 4(transport) of OSI and provides application (layer 7) protection with Azure Web Application Firewall.
- It provides detailed attack analytic reports during the attack in five-minute intervals and an after-action report for a complete summary of the event when the attack ends.
How does Azure DDoS Protection Standard Work?
Azure DDoS Protection Standard provides more capabilities than the Basic tier.
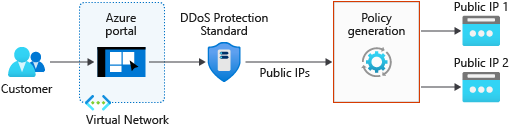
- When enabling DDoS Protection Standard, the first step is to create a DDoS Protection Plan and associate virtual networks to that plan. Only services with a public IP address on the virtual networks are protected.
- After configuring a DDoS protection plan, you need to assign a scope to the plan. You can select the services that will get DDoS Protection Standard by using your user-defined Azure Resource Groups, Management Groups, or Subscriptions.
- Your DDoS policy is generated from the DDoS protection plan. It’s autoconfigured and optimized by applying machine learning algorithms and using specific network traffic monitoring.
DDoS Standard Protection applies three mitigation policies—TCP SYN, TCP, and UDP—for each public IP address associated with a protected resource.

DDoS Protection reference architectures
These reference architectures are designed for the services that are deployed in the virtual network.
Applications running on load-balanced VMs
This reference architecture shows a set of proven practices for running multiple Windows VMs in a scale set behind a load balancer, to improve availability and scalability. This architecture can be used for any stateless workload, such as a web server.
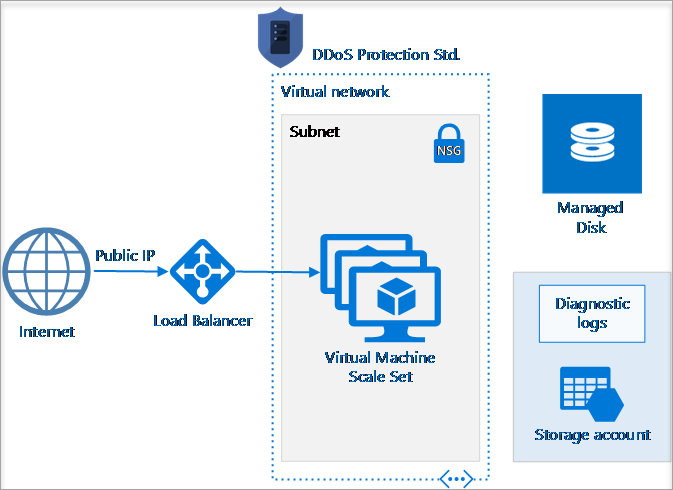
Applications running on Windows N-tier
There are many ways to implement an N-tier architecture. The following diagram shows a typical three-tier web application. The web and business tiers use load-balanced VMs.In this architecture, DDoS Protection Standard is enabled on the virtual network.

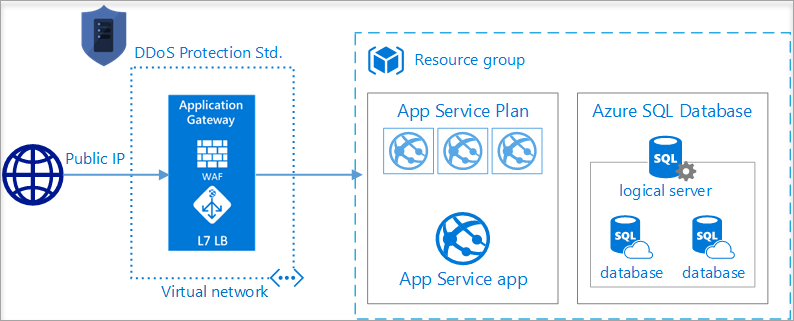
PaaS web application
This reference architecture shows running an Azure App Service application in a single region and shows a set of proven practices for a web application that uses Azure App Service and Azure SQL Database. Also, a standby region is set up for failover scenarios.
Comparison between DDoS Protection Basic & Standard Plans
| Feature | DDoS Protection Basic | DDoS Protection Standard |
| Active traffic monitoring & always on detection | Yes | Yes |
| Automatic attack mitigation | Yes | Yes |
| Availability guarantee | No | Yes |
| Cost Protection | No | Yes |
| Mitigation policies tuned to customer application | No | Yes |
| Metrics & Alerts | No | Yes |
| Mitigation Reports | No | Yes |
| Mitigation flow logs | No | Yes |
| DDoS rapid response support | No | Yes |
Features of DDoS Protection
Always-on traffic monitoring
DDoS Protection Standard monitors actual traffic utilization and constantly compares it against the thresholds defined in the DDoS Policy. When the traffic threshold is exceeded, DDoS mitigation is initiated automatically. When traffic returns below the thresholds, the mitigation is stopped.
DDoS mitigation policies
In the Azure portal, select Monitor > Metrics. In the Metrics pane, select the resource group, select a resource type of Public IP Address, and select your Azure public IP address. DDoS metrics are visible in the Available metrics pane.

Attack Analytics
Get detailed reports in five-minute increments during an attack, and a complete summary after the attack ends. Stream mitigation flow logs to Microsoft Sentinel or an offline security information and event management (SIEM) system for near real-time monitoring during an attack.
DDoS rapid response support
Microsoft has created a DDoS Protection rapid response team. You can contact this team for help during a DDoS attack and request a post-attack analysis. The DDoS Protection rapid response team follows the Azure Rapid Response support model. You can notify the team by opening a support request on the Azure portal and this feature is available only in the Standard plan.
Testing DDoS Protection
Testing is considered to be a vital part of how a system will perform during a DDoS attack. Azure customers can use an attack simulator for testing the performance of their protected services during a DDoS attack and these simulators are available on the BreakingPoint Cloud website(https://breakingpoint.cloud/).
We can use attack simulators to:
- To validate that our key services are protected during a DDoS attack.
- Practicing the incident response to a DDoS attack.
Preventing a DDoS Attack
Stopping an active DDoS attack can be difficult and may affect all legitimate users. Following the below-mentioned steps, it is preventive but better if we should also create an emergency DDoS incident response plan that will help out in times of emergency.
- Real-time packet analysis: Analyze packets based on different rules, as they enter our system, discarding the potentially malicious ones.
- DDoS defense system (DDS): A DDS can detect legitimate-looking content with malicious intent. It protects against both protocol and volumetric attacks, without requiring any human intervention.
- Web application firewall: Web application firewalls (WAF) are a great tool to mitigate application layer DDoS attacks. They give you a way to filter incoming requests, based on different rules, which can also be added on-the-fly, in response to an attack.
- Rate limiting: Limit the number of requests a server can entertain over a certain time period.
Pricing
A single Azure DDoS Protection Plan in a tenant can be used across multiple subscriptions. The DDoS Protection service will have a fixed monthly charge. The fixed monthly charge includes protection for 100 resources. Protection for additional resources will be charged on a monthly per-resource basis.
| Plans | Price |
|---|---|
| The monthly price for DDoS Protection (includes protection for 100 resources) | $2,944/month |
| Overage charges (more than 100 resources) | $29.5 per resource per month |
Pros & Cons of Azure DDoS Protection.
Pros:
- DDoS Protection acts like a backup whenever an attack happens & also provides risk mitigation against potential threats.
- Provides real-time metrics during attacks which can be used to analyze the attack.
- Configuring to Under DDoS attack or not will notify an alert when there’s active DDoS mitigation performed on public IP address.
Cons:
- Whenever an attack happens or is about to happen genuine users will not be able to find the information on the websites. The protection will activate once the malicious software doesn’t come up in the detection process.
- Due to the attack symptoms, the performance of the server will be slowed down and completely becomes halted.
Thanks for reading this blog!!