
Today, I’ll be sharing some information on Azure Sentinel, one of Azure’s general cloud security services.
What is Sentinel?
Microsoft Sentinel or Azure Sentinel is a cloud-native solution which provides:
- Security information and event management (SIEM): SIEM is an approach to security management that combines SIM (security information management: This is an automated tool used on enterprise data networks to centralize the storage and interpretation of logs and events generated by other network software) and SEM (security event management: SEM is primarily a security management technique used to analyze the data collected from security events) functions into one security management system.
- Security orchestration, automation, and response (SOAR): SOAR refers to a collection of software solutions and tools that allow organizations to streamline security operations in three key areas: threat and vulnerability management, incident response, and security operations automation.

Microsoft Sentinel delivers intelligent security analytics, threat intelligence across the enterprise and it provides a single solution for attack detection, threat visibility, proactive hunting, and threat response.
To use Sentinel, we need to have an Azure subscription for our account.
How does it function?
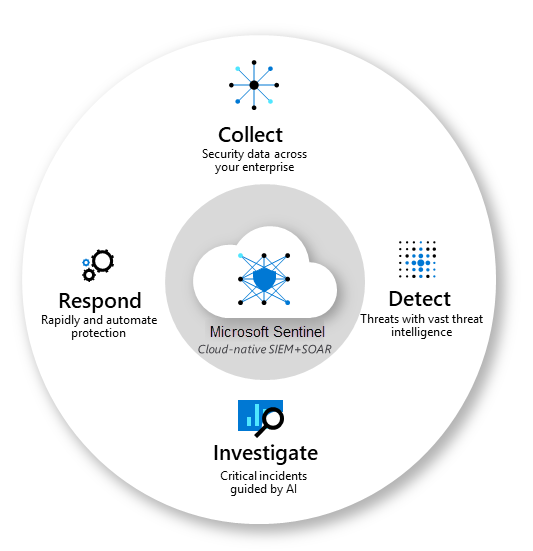
The basic functionality of Sentinel as a service is given below:
- Collect data: It collects data across the cloud using data connectors. Some examples of data connectors would be Microsoft 365 Defender, Microsoft Defender for Cloud, Office 365, Microsoft Defender for IoT, Azure Active Directory, Azure Activity, Azure Storage, Azure Key Vault, Azure Kubernetes service, and more. It also has connectors for Non-Microsoft solutions, enabling us to connect data sources with Sentinel.
- Detect threats: It can detect threats that weren’t previously detected and reduce the number of false positives using Microsoft’s analytics and threat intelligence system.
- Investigate threats: Sentinel investigates threats making use of Artificial intelligence and looks for suspicious activity based on years of research done by Microsoft in the cyber security field.
- Respond to threats: Sentinel is quick to respond to threats using automation and built-in orchestration. It provides users with the flexibility to create automated incident triggers and alert triggers along with automation rules.
To better understand, let’s look at the following scenario where we set up Sentinel to monitor threats.
We create a Virtual Machine and set it up to run a web application and a database server. Now, since we have an online application, there is traffic that has to be monitored and there’s data we need to keep secure. Now we can make use of the Sentinel service to detect threats and set a few automated rules and triggers which would quickly respond when some event takes place.
To set up Sentinel, we need to create a Workspace, to create and maintain logs and, Playbook for creating automated rules and triggers. Within the workspace, we have the option to create analytic rules, which can be used when working with the automation feature. With the automation rules, we can create rules to perform the tasks which need to be done daily.
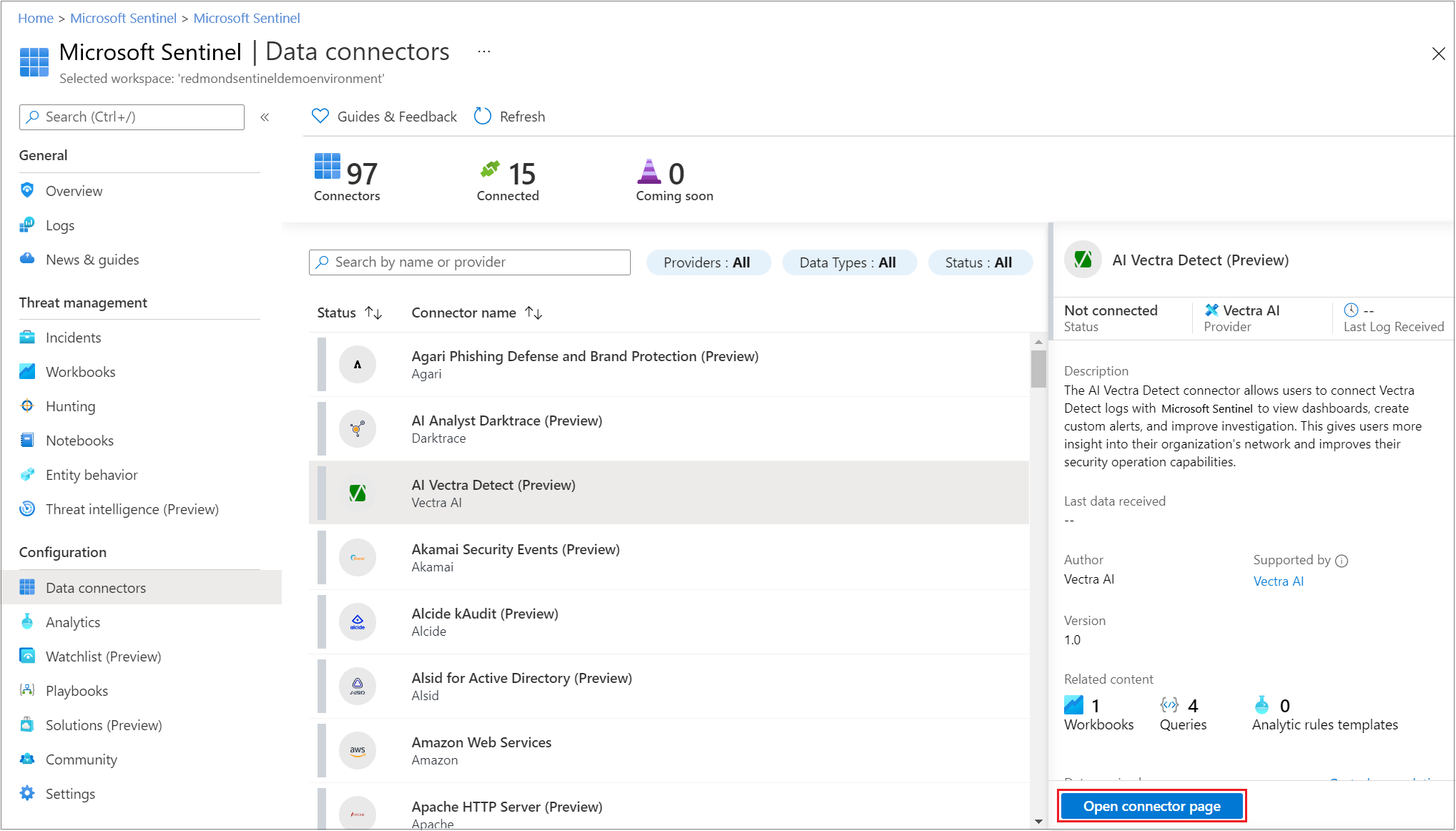
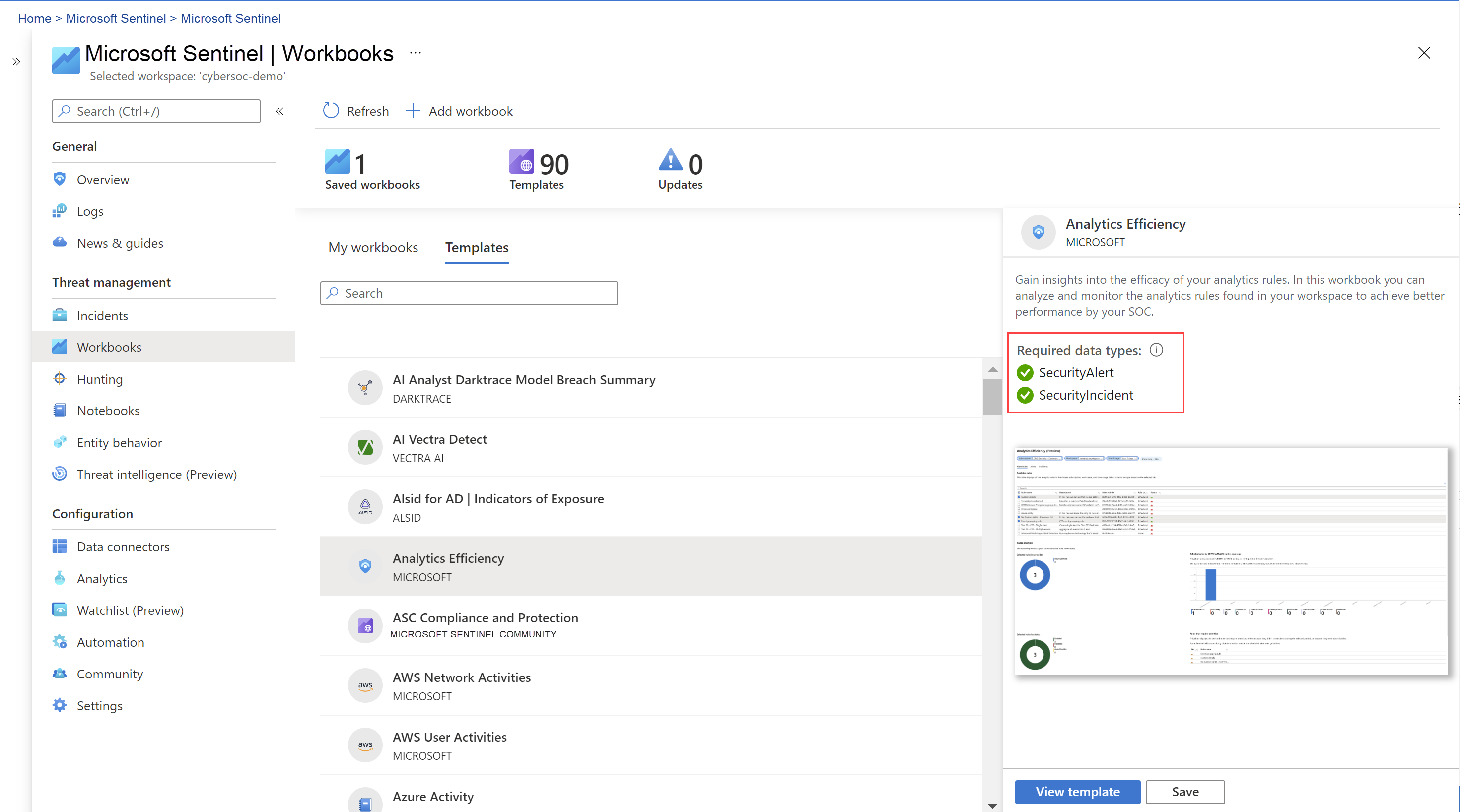
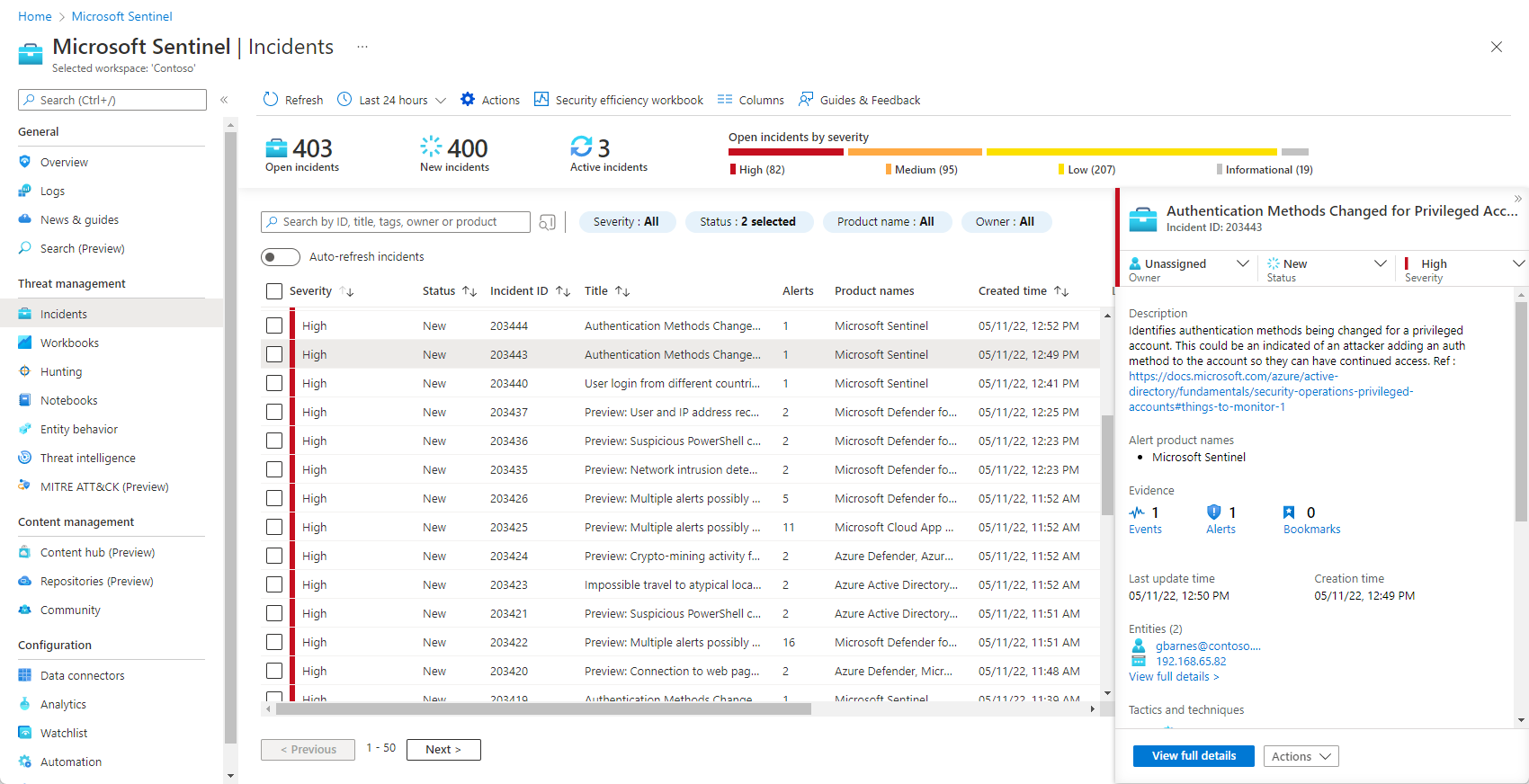

Overall, it gives a user flexibility to create automation rules and also analyzes the data to provide better and more efficient protection from threats.
Pricing Model
Lets look at the pricing model of Sentinel.
Initially, with any subscription, we get a 31-day trial period to use Sentinel and they come with few limitations. They are:
- New Log Analytics workspaces can ingest up to 10 GB/day of log data for the first 31-days at no cost. New workspaces include workspaces that are less than three days old. Both Log Analytics data ingestion and Microsoft Sentinel charges are waived during the 31-day trial period. This free trial is subject to a 20 workspace limit per Azure tenant.
- Existing Log Analytics workspaces can enable Microsoft Sentinel at no extra cost. Existing workspaces include any workspaces created more than three days ago. Only the Microsoft Sentinel charges are waived during the 31-day trial period.
Any service used beyond this will be charged as per the pricing model, which will be given below.
Sentinel’s price is mostly based on the amount of data that has been ingested from your data sources. The pricing is dependent on the type of logs used in the workspace which are Analytics Logs and Basic logs.
Analytics Logs
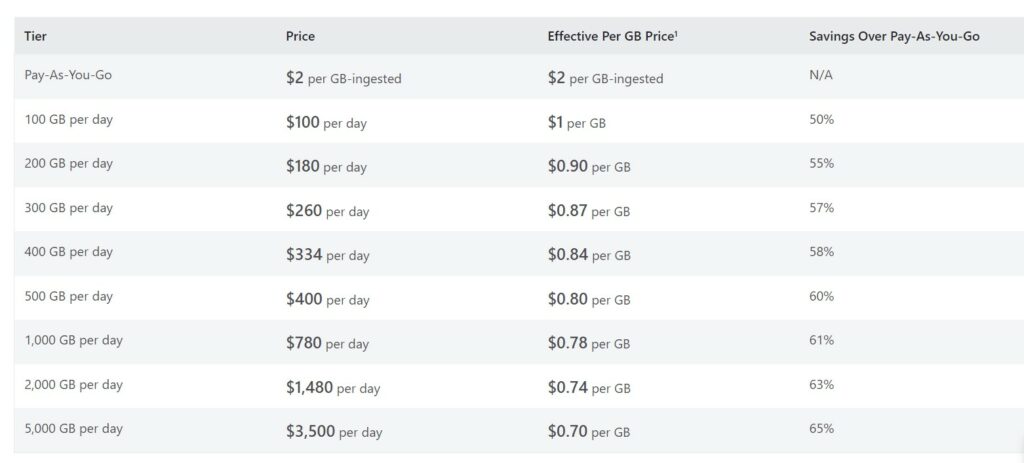
Analytics logs typically make up most of your high-security value logs. There are commitment tiers and there’s also a pay-as-you-go option.
- Pay-As-You-Go is the default model, based on the actual data volume stored and optionally for data retention beyond 90 days. Data volume is measured in GB.
- Commitment tier formerly known as Capacity Reservations offers capacities starting at 100GB per day. Any additional usage would be charged the same rate as the commitment tier rate.
The commitment tier offers flexibility where you can increase the limit anytime, and decrease the limit every 31 days, based on your requirement. The commitment tier costs much less when compared to the Pay-As-You-Go level, with a minimum savings percent of 50% and the highest of 65%.
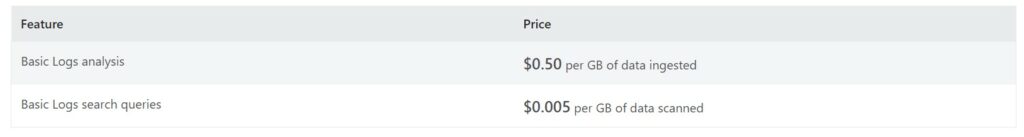
Basic Logs
Basic Logs have a much more reduced price and are charged at a fixed rate per GB used. They have the following limitations:
- Reduced querying capabilities
- Eight-day retention
- No support for scheduled alerts
Basic log Analysis costs $0.50 per GB ingested whereas, Basic log search queries are charged $0.005 per GB searched. Basic logs are accessible for 8 days period for interactive queries. After that period archived logs can be used for storing the data.
Log Data
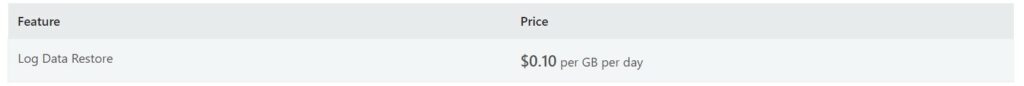
Microsoft Sentinel offers an archiving solution for logs that can be stored and analyzed based on our requirements. We can store archive data for up to 7 years.
- We have an option to restore log data for analysis and they are restored for $0.10 per GB per Day.
The pricing model may vary from region to region. For more information please check Sentinel Pricing.
Pros & Cons
Now we will discuss the pros and cons of using Microsoft Sentinel.
Pros
The following are some of the pros of using Sentinel:
- Use of Artificial Intelligence
- Threat analysis
- Automation for quick response
- Reduction of false positives
- Easy to log Analysis rules
- Excellent tools for cleaning data, sorting out irrelevant log data, and fixing log data
- Non-Microsoft product integration
- User friendly UI
Cons
The following are the cons of using Sentinel:
- Dependence on Azure software
- Send alerts to Mobile Device
- Mobile application which can be used to investigate anytime and anywhere
- No additional capacity to connect SIEMs
- Can be expensive for small sized businesses
Alternatives
Let’s look at some of the alternative SIEM services.
According to G2 these are some of the top alternates for Microsoft Sentinel:
- IBM Security QRadar
- Sumo Logic
- Splunk Enterprise Security
- Datadog
- LogRhythm NextGen SIEM platform
As per the reviewers these are better in terms of
- Support
- Better at meeting requirements
The above mentioned services are deemed to be more expensive than Sentinel.
Conclusion
After going through the reviews and trying to setup the services, I’ve found that:
- Sentinel provides a top-quality solution for incident and event management
- With both incident and event management tools combined in one tool, it makes it easier for users to analyze data
- The use of AI to investigate threats and make use of data from research is really a plus
- Automation allows users to focus on other areas which might need attention
- Sentinel is perfect for medium to large scale business who have larger data load
- It is easier for users accustomed to these services, but a new user might find it difficult to work with
Overall, Microsoft Sentinel provides great solutions for security related issues and since its relatively young in terms of security solutions, we can expect it to improve over the course of time.
Thank you for reading!!