Basics of Secure Shell or SSH
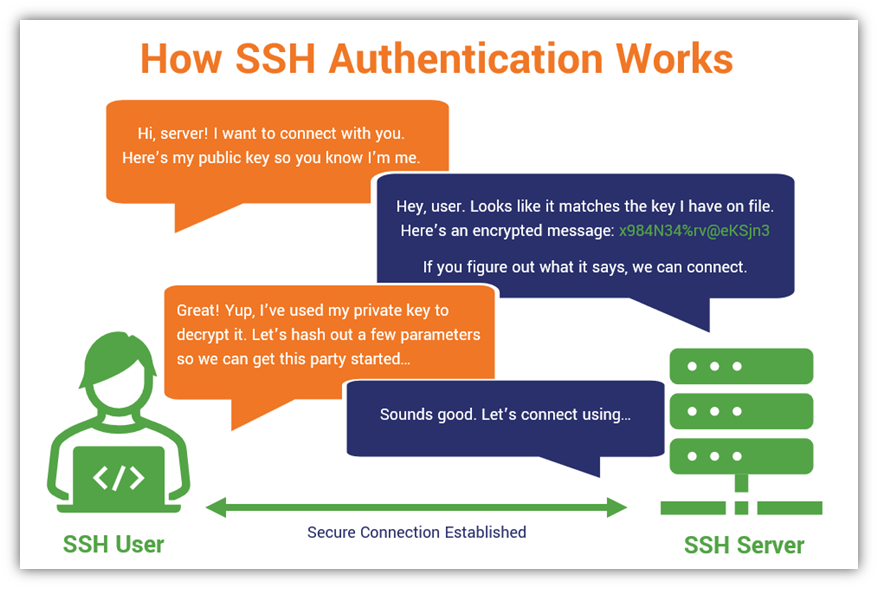
SSH or Secure Shell is a secure network protocol which allows secure authentication and data communications with a remote system, like a server or another PC. SSH is used to create a safe tunnel to the remote systems to transfer files or run commands. SSH has SFTP (Secure File Transfer Protocol) and SCP (Secure Copy) protocol within to facilitate this in a secure way. This capability of SSH has become more important in the past few years thanks to advances in cloud computing.
Secure Shell creates a command line environment to the remote system through which commands can be executed, rather than on the computer that you are sitting at.
For an IT admin or if your personal project needs you to connect to multiple cloud virtual machines then managing multiple key pairs in a secure manner becomes important.
Managing Key Pairs
Managing key pairs is important because if you misplace your keys, you will lose access to your remote systems. This would mean extra administrative effort of creating a new key pair and updating in all your remote system so that the SSH connection can be established successfully. If key pairs are properly managed, authentication via SSH keys is more secure than traditional passwords, since SSH keys are resistant to brute force attacks.
Having an effective key management would mean that you have full visibility of all your access keys, which keys are being used to access which resources and being able to know which keys are obsolete so that they can be removed.
Also, SSH key mismanagement could leave your application non-compliant to government regulations like GDPR and HIPAA.
SSH Key Pair Management Best Practices
It’s really important how you manage your keys, since any rouge actor which gets access to your keys could connect your remote system with ease. I have tried to compile a few best practices which you could follow for your application.
- Having a passphrase: It’s important to add a passphrase when you create a new Key Pair since this would provide an additional layer of security for you. The passphrase is used to encrypt your private key so that only with the right passphrase the private key can be decrypted. So, if a hacker was able to obtain a copy of the file of your key, it will be encrypted and unusable.
- Storage of keys: It is important how you store your keys. It is not advisable to store your keys as a plain file in your system. If your hard drive were to get corrupted, you would lose your keys which in turn would lead to loss of access to your remote systems. I would suggest coming up with your own system to keep your keys secure or you could make use of the key management systems provided by the cloud service providers. I talk about this later on in the blog.
- Don’t reuse keys: Reusing your keys for different remote systems is never a good practice. In an ideal scenario, each user in your application should have a different key to each system. This way if a key is compromised, your whole system will not be exposed. For your personal projects, it should be easy enough manage the different keys to different cloud resources. But if you want to scale your project, you will need to look into key management system to keep track of the different keys that are being used and by whom.
- Tracking usage: It is important to keep track of which keys are being used to access which resources in your application. This way you could identify if a key is being used to access something it shouldn’t, you could then revoke the access then.
- Renewing keys: It is advisable to renew your keys with a fresh pair every 6 months to keep your application secure in case there are any compromised keys.
SSH Clients
A lot of your key pair management would depend on how you plan to connect to your remote systems. The most basic way will be to be use a command line interface to directly connect to the remote system. Most operating systems nowadays come with inbuilt support for SSH which could be utilized. But using a command line may not be easy for every user. An SSH client can be used in such a case and is generally the most preferred way. A descent SSH client will have a basic key management system, a one-click connection to the remote systems command line interface and support for file transfer using SFTP via the SSH. If you have completed hands-on project 1, you would have used Bitvise. Bitvise is a free SSH client having the features we discussed earlier and more. It is available for both Windows and macOS. If you are looking for client which can be used on the go, then you could look at JuiceSSH for Android and Termius for iOS.
Now there are certainly more SSH client applications in the market but check if your requirements are met before committing to one. A little research will lead to having a seamless SSH experience for you.
Key Management systems provided by Cloud providers
Managing different keys for your application can become difficult quickly when your application starts to grow. If your current key management isn’t meeting your needs, you could always make use of the key management services provided by your cloud service providers. During the HOP 1 exercises, Azure’s Key Vault and AWS’s Key Pairs were used to upload the keys that we generated. These services also offer additional services like generating new key pairs, tracking which instances are using which key pairs and other detailed logging services. The logging service will be really helpful when you start to have more users for your application since you keep track of who is using which keys and for renewing and replacing keys.
Both Azure and AWS have provided extensive documentation on their key management services and its advanced features. I provided the link for the same below:
Azure Key Vault: https://learn.microsoft.com/en-us/azure/security/fundamentals/key-management
AWS Key Pairs: https://docs.aws.amazon.com/AWSEC2/latest/UserGuide/ec2-key-pairs.html
References:
- https://www.comparitech.com/net-admin/getting-started-with-ssh/
- https://winscp.net/eng/docs/ssh_keys
- https://www.ssh.com/academy/ssh/public-key-authentication
- https://www.comparitech.com/net-admin/getting-started-with-ssh/#How_to_Get_SSH (this page also has a SSH command cheat sheet and common troubleshooting tips)